Is your cybersecurity really covering all the bases?
OpenText Information Management
NOVEMBER 15, 2024
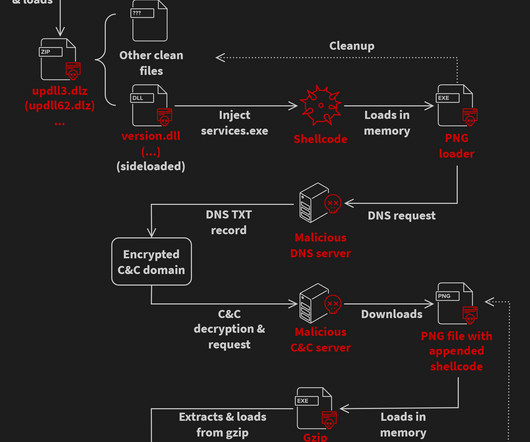
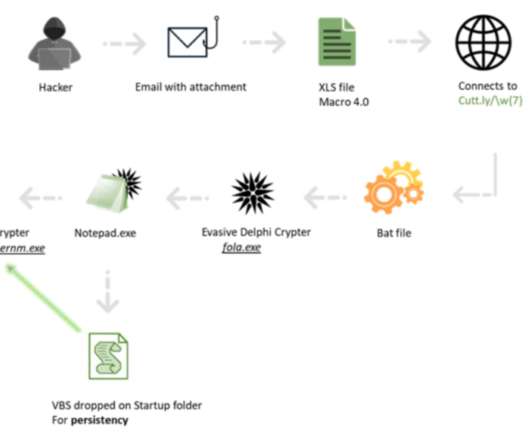
If your security strategy is limited to one line of defense, you’re missing out on a holistic approach that goes beyond just threat detection and response. Digital forensics and investigation : When a cyber incident occurs, it’s not just about cleanup. Vulnerabilities within application code are gold mines for attackers.









Let's personalize your content