Shared Drive Cleanup Success Story
The Texas Record
JANUARY 25, 2019
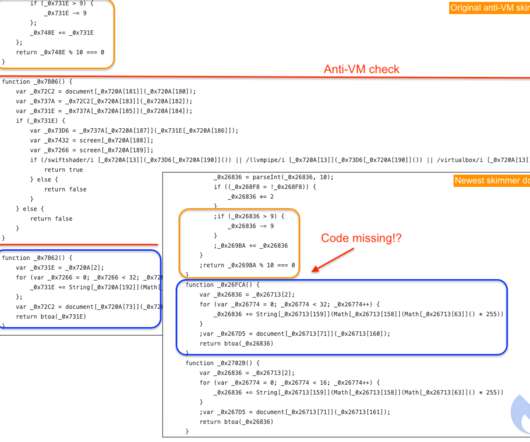
The departmental structure of the ARIS division at the Texas State Library and Archives Commission (TSLAC). The standards were influenced by recommendations from the committee that is leading our division’s shared drive cleanup as well as other best practices for naming electronic records. 4) Maintain.























Let's personalize your content