Security Affairs newsletter Round 487 by Pierluigi Paganini – INTERNATIONAL EDITION
Security Affairs
SEPTEMBER 1, 2024
CISA adds Google Chromium V8 bug to its Known Exploited Vulnerabilities catalog Young Consulting data breach impacts 954,177 individuals BlackByte Ransomware group targets recently patched VMware ESXi flaw CVE-2024-37085 US offers $2.5M reward for Belarusian man involved in mass malware distribution U.S.



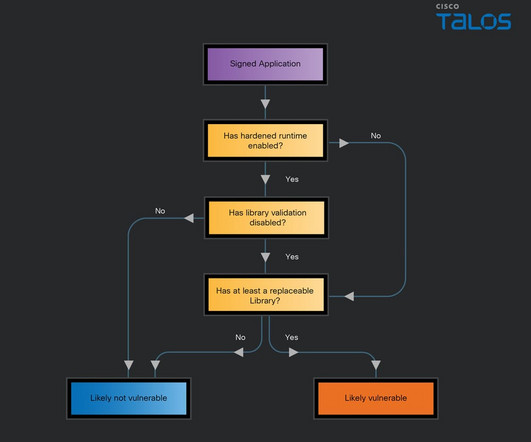






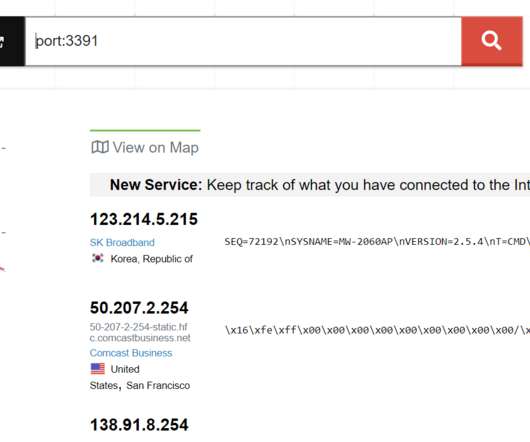























Let's personalize your content