New Ransomware Actor 8Base Rivals LockBit in Extortion
Data Breach Today
JUNE 29, 2023
The group's top targets include business services, finance, manufacturing and IT industries.
This site uses cookies to improve your experience. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country, we will assume you are from the United States. Select your Cookie Settings or view our Privacy Policy and Terms of Use.
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
Used for the proper function of the website
Used for monitoring website traffic and interactions
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.

Data Breach Today
JUNE 29, 2023
The group's top targets include business services, finance, manufacturing and IT industries.
Security Affairs
MAY 5, 2021
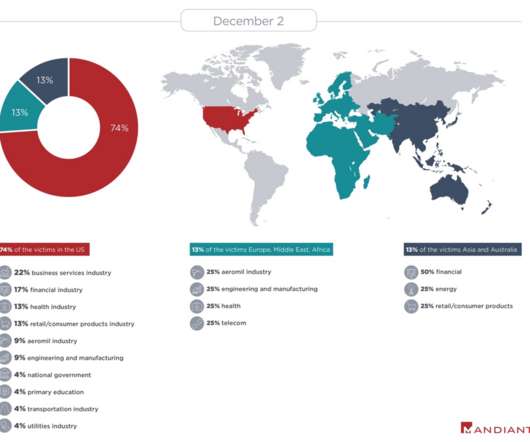
.” At the time of the report, although Mandiant has no evidence about the purposes of the attacks, the broad targeting across multiple industries and the choosing of targets of a global scale, suggests that the attackers could be financially motivated. ” Follow me on Twitter: @securityaffairs and Facebook.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.
Security Affairs
DECEMBER 13, 2021
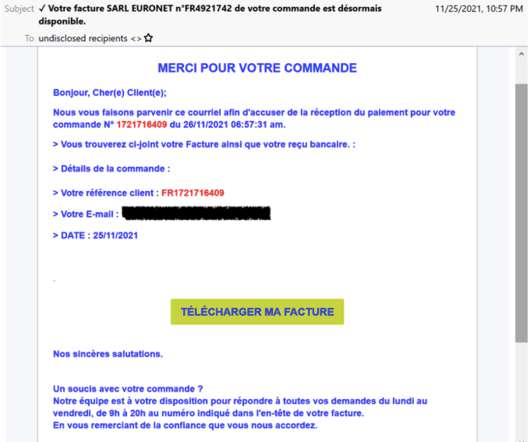
The TinyNuke malware is back and now was used in attacks aimed at French users working in manufacturing, technology, construction, and business services. The attackers used invoice-themed lures targeting entities in manufacturing, industry, technology, finance, and other verticals. . .”

Security Affairs
JULY 6, 2020
Xchanging is a business process and technology services provider and integrator, which provides technology-enabled business services to the commercial insurance industry.
Security Affairs
NOVEMBER 19, 2023
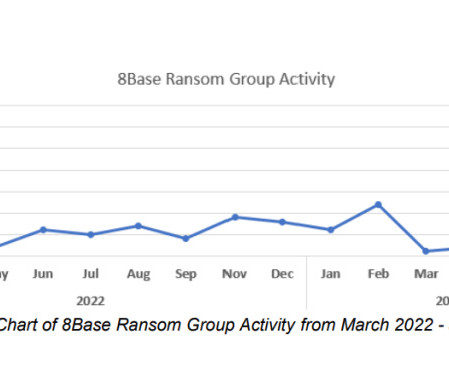
The group has been active since March 2022, it focused on small and medium-size businesses in multiple industries, including finance, manufacturing, business services, and IT. The experts observed a massive spike in activity associated with this threat actor between May and June 2023. and Brazil.
Security Affairs
JUNE 28, 2023
The group has been active since March 2022, it focused on small and medium-size businesses in multiple industries, including finance, manufacturing, business services, and IT. “8Base has an opportunistic pattern of compromise with recent victims spanning across varied industries.” and Brazil.
Krebs on Security
FEBRUARY 22, 2024
Experts say the leak illustrates how Chinese government agencies increasingly are contracting out foreign espionage campaigns to the nation’s burgeoning and highly competitive cybersecurity industry. “The infosec industry is always trying to distinguish [the work] of one APT group from another. ”

Security Affairs
OCTOBER 5, 2021
Syniverse service provider discloses a security breach, threat actors have had access to its databases since 2016 and gained some customers’ credentials. Syniverse is a global company that provides technology and business services for a number of telecommunications companies as well as a variety of other multinational enterprises.

Security Affairs
SEPTEMBER 28, 2018
The Port has mobilized a team of industry experts and local, regional, state and federal partners to minimize impacts and restore system functionality, with priority placed on public safety-related systems. The Port first received reports of the disruption on Tuesday, September 25, 2018.

Thales Cloud Protection & Licensing
JULY 24, 2023
Network Encryption Keeps Our Data in Motion Secure for Business Services madhav Tue, 07/25/2023 - 04:59 The demand for high-speed networks and fast data transfers is increasing due to cloud adoption, digital transformation, and hybrid work. Why do you need network encryption in business services?

CILIP
DECEMBER 2, 2024
CILIP has written to Alison McGovern MP the Minister for Employment at the Department for Work and Pensions; Richard Pennycook CBE the Interim Chair of Skills England, and to every member of the House of Lords Industry and Regulators Committee.

IBM Big Data Hub
MARCH 20, 2024
For highly regulated industries, these challenges take on an entirely new level of expectation as they navigate evolving regulatory landscape and manage requirements for privacy, resiliency, cybersecurity, data sovereignty and more. This means actively minimizing downtime and closing gaps in the supply chain to remain competitive.

The Last Watchdog
SEPTEMBER 23, 2024
Vercara’s industry-recognized UltraDNS product is an enterprise-grade managed authoritative DNS service that securely delivers fast and accurate query responses to websites and other vital online assets, ensuring 100% website availability along with built-in security for superior protection. For more information, visit ?

IT Governance
SEPTEMBER 30, 2022
The other most vulnerable sectors were business services (23), construction (22), manufacturing (19) and transport (18). The second criteria [sic] is more straightforward and primarily deals with the depth of the company’s pockets and how lacking in cyber defenses their business is. Why are small businesses at risk?

OpenText Information Management
FEBRUARY 4, 2025
By simplifying and automating fundamental identification processes, this release enables businesses to access the core collection of OpenText identity and access management capabilities under a single set of integrated microservices. Faster MTTR and minimized service interruptions from networking changes. The result?

The Security Ledger
SEPTEMBER 14, 2022
The phrase was intended to capture the trend of formerly brick and mortar businesses – indeed, entire industries- shifting to a software and services model. Writing in 2011 i n the Wall Street Journal , Andreessen predicted that, in the next 10 years, he expected many more industries to be disrupted by software. .

IBM Big Data Hub
MAY 13, 2024
Artificial intelligence (AI) represents a once-in-a-lifetime change management opportunity that might decide who wins and losses across every industry. To prepare their people and businesses, organizations must ensure that their employees are equipped with the skills for tomorrow without disrupting today’s business.
eSecurity Planet
MARCH 27, 2023
” The three activity sets included a campaign against the Philippine government between March and May 2022; a campaign against telecommunications and business service providers in South Asia in April 2022; and a campaign against organizations in Belarus and Russia in May 2022.

Rocket Software
MARCH 11, 2022
According to research by Aberdeen, the industries with the strongest need for terminal emulation are business services (accounting, HR and consulting, for example), manufacturing, retail, education, healthcare, finance and insurance. Improve experiences.

CGI
FEBRUARY 19, 2019
Innovation in business models requires collaboration with partners that have complementary capabilities and assets. Fortum Charge & Drive, for instance, provides open APIs for operators to build their business services on top of its EV charging platform, facilitating a connected network of 1,400 affiliated smart chargers.

Data Matters
FEBRUARY 28, 2019
For one, many had defined the threat landscape too narrowly. What can we, as a Board or Management Committee, do to make sure the firm’s second line of defence is able to provide effective challenge to the first line on cyber-related matters?

Info Source
OCTOBER 12, 2018
To respond, incumbent banks are investing in next-generation technologies, with the global banking industry spending $519 billion on IT this year, up 4.1 Many traditional institutions are still in a tug of war with fintechs and digital challenger banks. percent year on year, from $499 billion in 2017 according to Gartner.

IT Governance
JULY 9, 2024
You should also check the business/service continuity guarantees. If you’re relying on a third-party service provider to provide you with your data, and that third party suffers an outage – for whatever reason – how does that impact you, as the data controller? So, don’t be scared to go back and challenge it.

Interactive Information Management
MARCH 4, 2015
The DaaS Consumer - who needs not only to acquire data from somewhere (in a way that shields them from the underlying technology concerns), but also then may use it to develop information apps and services, or repackage the data to share further with others. The consumer assigns and realizes value from the service.

OpenText Information Management
JULY 27, 2023
In this series of blogs, we have been considering the following key points that help to not only manage resistance but to convert resistance into support: Consider resistance as a natural reaction to change Distinguish between hesitancy and resistance Detect signs of resistance Identify the root causes of resistance Manage resistance Communicate, communicate, (..)

Thales Cloud Protection & Licensing
MARCH 8, 2018
In addition, the DSM is starting to support a number of new business services as well. Across regions and industries, the use of KMIP is set to see explosive growth. Following are a couple examples: Smart grids. In the utilities sector, the DSM is used in KMIP implementations that support smart grids, and the scale is massive.

Info Source
JUNE 7, 2018
ECM is one the top ten high-tech topics right now, as the Bitkom industry barometer 2018 reports. These new customers come from a wide range of industries. Coinciding with the growth in licensing business, service business has also jumped by over 11%. The positive flux of new orders continues in 2018 for SER.

eSecurity Planet
JULY 11, 2023
Image credit: Kolide Kolide specifically focuses on the devices attempting to access business services. Kolide doesn’t automatically trust devices until they demonstrate compliance with its policies, which users can configure in accordance with their business’s security strategy.

CGI
NOVEMBER 14, 2016
Whether it’s an industrial accident, transport disaster or how little Jonny had his tooth knocked out, the sequence of events is much the same; shock at what has occurred, hasty judgements as to the cause and then an extended period of investigation to identify lessons to avoid it happening again. Don’t blame ‘The Things’. p.butler@cgi.com.

CILIP
MARCH 20, 2025
Exploring a library role in the publishing ecosystem Relationships between readers and writers are brokered by a multi-billion pound global industry. What happens if libraries step into the local knowledge gap? Here Rebecca Gediking, Head of Libraries at GLL, explains how theyre planning to do it.

Reltio
SEPTEMBER 9, 2019
Tony Saldanha is the President of Transformant and a globally recognized information technology and shared services executive. I’ve had the great fortune of evolving with the IT and shared service industry across 6 countries and 13 different roles and assignments. What is the role of data governance in these processes?

eSecurity Planet
AUGUST 9, 2023
While MSPs also provide a wide range of business services, here we’ll focus on managed IT and cybersecurity service providers. Organizations easily enter into ad hoc relationships with contractors or with a service provider for common services that have established, public pricing.

eSecurity Planet
AUGUST 9, 2023
While MSPs also provide a wide range of business services, here we’ll focus on managed IT and cybersecurity service providers. Organizations easily enter into ad hoc relationships with contractors or with a service provider for common services that have established, public pricing.

Data Protection Report
AUGUST 11, 2022
Financial institutions should consider submitting comments directly, or working with industry associations, to provide comments to the NYDFS during the initial comment period.

OpenText Information Management
MARCH 19, 2024
We’ve seen countless headlines over the past few years about the skills gap and the talent shortage. According to Forbes , “from increased job satisfaction and loyalty to better retention rates—and ultimately better employees—continued learning benefits everyone involved.”

Info Source
FEBRUARY 13, 2018
Combining Vera’s strong security and dynamic control with Canon Solutions America’s innovative digital and business services platform, customers will now have access to powerful new security capabilities, designed to give users dynamic access control over their files.

OpenText Information Management
FEBRUARY 1, 2024
The name says it all, because microlearning refers to learning in small learning units. Instead of working with an extensive training manual or participating in a full-day seminar, microlearning allows individuals to absorb very compressed portions of knowledge in just a few minutes. … The post What is Microlearning?

Hunton Privacy
AUGUST 15, 2022
Covered entities must implement a written policy requiring industry-standard encryption to protect nonpublic information held or transmitted by the covered entity both in transit over external networks and at rest. The risk assessments required by Section 500.9 A covered entity’s incident response plan, as required by Section 500.16

OpenText Information Management
MARCH 10, 2023
Managing user resistance can be challenging and there can be many reasons for this resistance. However, it would be wrong to treat users as if they are the problem and then to develop a defense mechanism around their resistance. It is rather, an opportunity to help people transition through the change.

OpenText Information Management
FEBRUARY 13, 2023
As technology and business processes continue to evolve, it’s crucial to invest in building the skills of your employees. This investment ensures they possess the skills needed to succeed now and in the future.

Interactive Information Management
OCTOBER 7, 2013
A colocation strategy for your local business IT assets and services simply means hiring and trusting a local Data Center (an IT Services Provider and Facility) to own, operate and manage the commodity IT and computer server facilities.
OpenText Information Management
MAY 31, 2023
In this series of three blogs on managing user resistance when implementing software, we are considering the following key areas that help to not only manage resistance but to also convert resistance into support: Consider resistance as a natural reaction to change Distinguish between hesitancy and resistance Detect signs of resistance Identify the (..)

Info Source
MAY 30, 2024
Service bureaus that only provide basic capture services will increasingly struggle and may become acquisition targets if their customer base or assets are attractive for other vendors. Nations, industries, and regions that are already advanced will accelerate their digital investments.

Security Affairs
FEBRUARY 11, 2025
The 8Base ransomware group has been active since March 2022, it focused on small and medium-size businesses in multiple industries, including finance, manufacturing, business services, and IT. In November 2023, Cisco Talos researchers observed 8Base ransomware operators using a new variant of the Phobos ransomware.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content