How digital fax and capture are transforming healthcare
OpenText Information Management
FEBRUARY 15, 2024
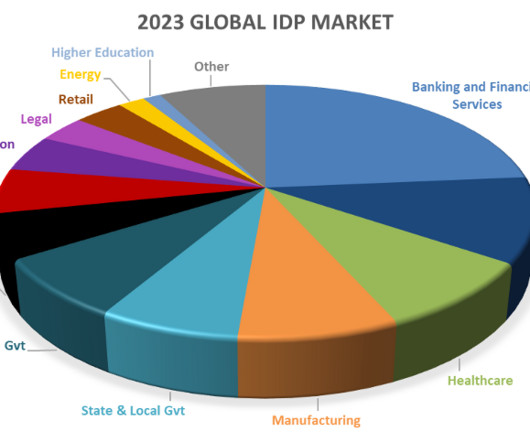
The compound annual growth rate of healthcare data will reach 36% by 2025 – rising 6% faster than manufacturing, 10% faster than financial services and … The post How digital fax and capture are transforming healthcare appeared first on OpenText Blogs.














































Let's personalize your content