The Life Cycle of a Breached Database
Krebs on Security
JULY 29, 2021
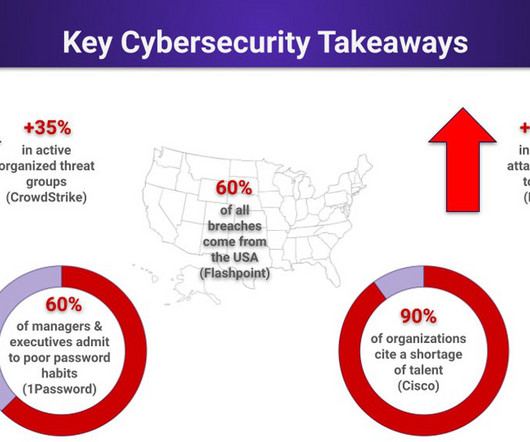
Our continued reliance on passwords for authentication has contributed to one toxic data spill or hack after another. There, denizens with computer rigs that are built primarily for mining virtual currencies can set to work using those systems to crack passwords. started receiving emails with a “cash back” offer.

















Let's personalize your content