e-Records 2017: “Establishing Information Governance for Local Governments in Microsoft SharePoint and Office 365”
The Texas Record
DECEMBER 4, 2017
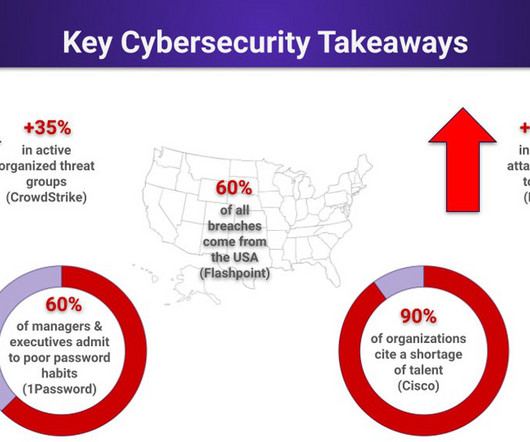
Information Governance: Take Control and Succeed. Establishing Information Governance for Local Governments in Microsoft SharePoint and Office 365. Involve your stakeholders in your Information Governance Plan. Train everyone. Continue training users, site owners, and new staff. Mr. Webb and Ms.


























Let's personalize your content