A massive phishing campaign using QR codes targets the energy sector
Security Affairs
AUGUST 16, 2023
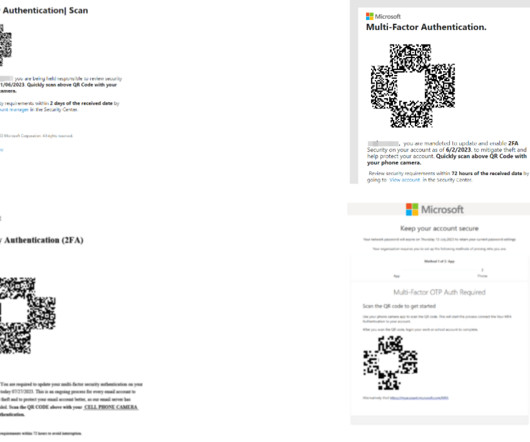
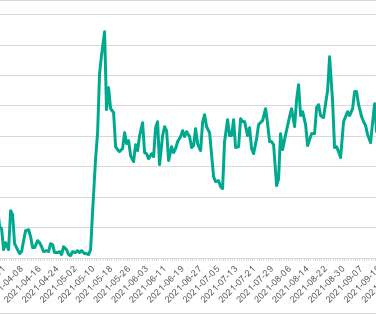
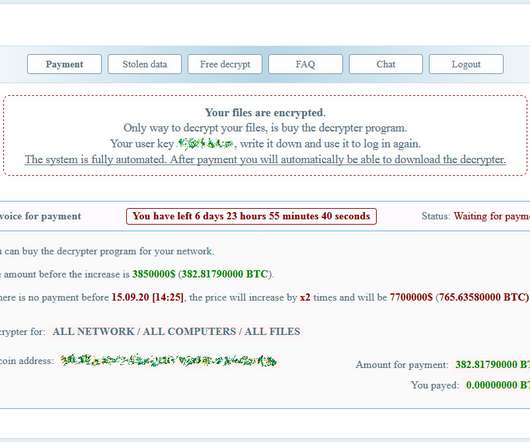
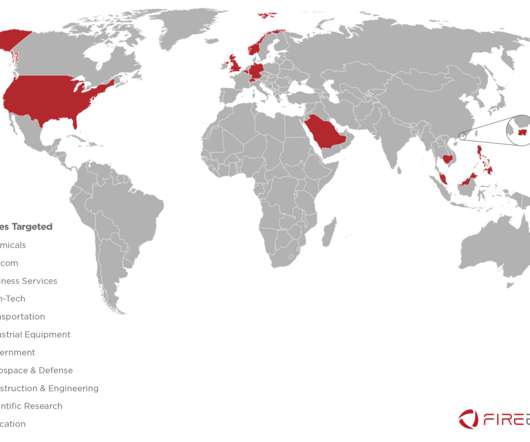
A phishing campaign employing QR codes targeted a leading energy company in the US, cybersecurity firm Cofense reported. “Beginning in May 2023, Cofense has observed a large phishing campaign utilizing QR codes targeting the Microsoft credentials of users from a wide array of industries.” ” continues the report.




























Let's personalize your content