Education Sector OnDemand | Authentication for the Evolving Campus Community
Data Breach Today
MARCH 10, 2021
Smart & Adaptive MFA for the Modern Campus View this webinar as we discuss multi-factor authentication for the evolving campus community.
This site uses cookies to improve your experience. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country, we will assume you are from the United States. Select your Cookie Settings or view our Privacy Policy and Terms of Use.
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
Used for the proper function of the website
Used for monitoring website traffic and interactions
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.

Data Breach Today
MARCH 10, 2021
Smart & Adaptive MFA for the Modern Campus View this webinar as we discuss multi-factor authentication for the evolving campus community.
Security Affairs
AUGUST 31, 2023
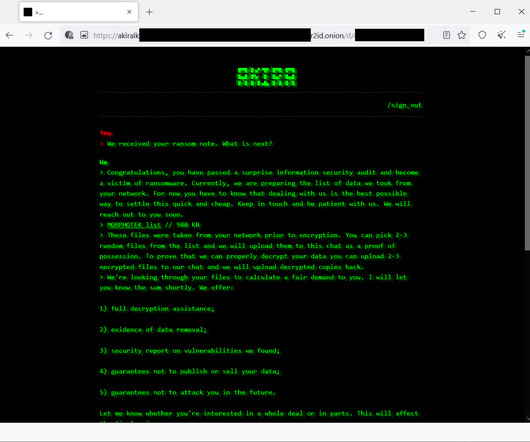
Cisco is aware of attacks conducted by Akira ransomware threat actors targeting Cisco ASA VPNs that are not configured for multi-factor authentication. “This highlights the importance of enabling multi-factor authentication (MFA) in VPN implementations. . ” reads a post published by Cisco PSIRT. 200 and 162.35.92[.]242
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.
Security Affairs
FEBRUARY 16, 2025
Storm-2372s targets during this time have included government, non-governmental organizations (NGOs), information technology (IT) services and technology, defense, telecommunications, health, higher education, and energy/oil and gas in Europe, North America, Africa, and the Middle East.” ” continues the report.
Security Affairs
NOVEMBER 21, 2023
Experts warn of a surge in NetSupport RAT attacks against education, government, and business services sectors. The most impacted sectors are education, government, and business services. These infected websites host a PHP script which displays a seemingly authentic update. implacavelvideos[.]com).

Advertiser: ZoomInfo
Marketing and sales teams are feeling pressured to deliver authentic messaging to buyers at every point of their customer journey. Database benchmarks for education and resource prioritization. 47% of marketers said they have a database management strategy in place, but there is room for significant improvement.

Security Affairs
APRIL 25, 2023
Google announced that its Authenticator app for Android and iOS now supports Google Account synchronization. Google announced that its Google Authenticator app for both iOS and Android now supports Google Account synchronization that allows to safely backup users one-time codes to their Google Account.

Security Affairs
SEPTEMBER 7, 2022
In the digital age, authentication is paramount to a strong security strategy. Which are the challenges of user authentication? In the digital age, authentication is paramount to a strong security strategy. User authentication seems easy, but there are inherent challenges to be aware of. User Authentication.

Security Affairs
DECEMBER 19, 2024
.” The experts added that FortiWLM’s verbose logs expose session IDs, enabling attackers to exploit log file read vulnerabilities to hijack sessions and access authenticated endpoints. Authenticated users’ session ID tokens in FortiWLM remain static per device boot. ” concludes the report.

Security Affairs
MAY 26, 2022
Security researchers released PoC exploit code for the critical authentication bypass vulnerability CVE-2022-22972 affecting multiple VMware products. VMware Workspace ONE Access, Identity Manager and vRealize Automation contain an authentication bypass vulnerability affecting local domain users.” using CVE-2022-22972.

Security Affairs
SEPTEMBER 6, 2023
A Reddit user with the handle ‘Educational-Map-8145’ published a proof of concept exploit for a zero-day flaw in the Linux client of Atlas VPN. The Reddit user pointed out that the client does not support any authentication mechanism. It does not have ANY authentication.

Data Breach Today
JULY 8, 2020
Joni Brennan on Identity Being Core to a Socioeconomic Safety Net Joni Brennan, president of the Digital ID & Authentication Council of Canada (DIACC), says identity management is a core component to building a solid foundation for a socioeconomic safety net, particularly during a pandemic.

Security Affairs
SEPTEMBER 18, 2024
Enable 2FA Authentication: This measure adds an extra layer of security by requiring a second factor of authentication in addition to the password. Always verify the authenticity of received communications. Education improves awareness” is his slogan.

Security Affairs
NOVEMBER 14, 2021
Other important protections are: 1) rigorous authentication procedures; and 2) a company policy that requires passwords for employee credentials and administrative functions to be l-o-n-g and complex.” ” states the FTC. ” The FTC also shared guidance for businesses that experienced a data breach.

Security Affairs
APRIL 26, 2024
In addition, cryptocurrency exchange platforms are implementing more stringent security measures, such as two-factor authentication and advanced encryption, to protect users’ funds. Educate and protect users and investors To effectively counter cybercrime, it is essential to understand the nature and techniques used by criminals.

Security Affairs
JANUARY 13, 2024
An unauthenticated, remote attacker can exploit the vulnerability to conduct a brute force attack in an attempt to identify valid username and password combinations or an authenticated, remote attacker to establish a clientless SSL VPN session with an unauthorized user. Cisco investigated the hacking campaign with the help of Rapid7.

Security Affairs
OCTOBER 2, 2023
It was a bit shocking that we were able to reach the deserialization sink without any authentication.” Most of these online assets belong to large enterprises, governments and educational institutions.” All versions of WS_FTP Server are affected by these vulnerabilities.” ” reads the advisory published by Assetnote.
Security Affairs
SEPTEMBER 24, 2023
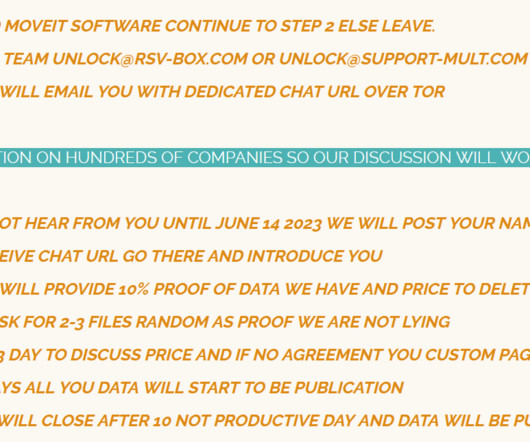
educational nonprofit organization National Student Clearinghouse disclosed a data breach that impacted approximately 900 US schools. a SQL injection vulnerability has been found in the MOVEit Transfer web application that could allow an un-authenticated attacker to gain unauthorized access to MOVEit Transfer’s database.”

Security Affairs
SEPTEMBER 8, 2023
An unauthenticated, remote attacker can exploit the vulnerability to conduct a brute force attack in an attempt to identify valid username and password combinations or an authenticated, remote attacker to establish a clientless SSL VPN session with an unauthorized user.

Security Affairs
FEBRUARY 4, 2022
billion Azure AD brute force authentication attacks and detected 35.7 Enabling multi-factor authentication (MFA) and passwordless authentication would allow customers to protect their accounts from brute force attacks. billion Azure AD brute force authentication attacks and intercepted 35.7 ” states Microsoft.

The Last Watchdog
OCTOBER 15, 2019
Related: The Internet of Things is just getting started The technology to get rid of passwords is readily available; advances in hardware token and biometric authenticators continue apace. Push’ authentication So how do companies even begin to think about getting rid of passwords? million on average, a potentially crippling amount.

Security Affairs
DECEMBER 9, 2020
The most common algorithms are those patented by RSA Data Security: This algorithm, also called asymmetric key cryptography, provides a pair of keys (a public and private key) associated with an entity that authenticates the identity of the key itself. Hash encryption is used to ensure integrity and authentication. The hash function.

Security Affairs
JULY 21, 2019
US Department of Education warned that hackers have breached at least 62 college and university networks by exploiting a vulnerability in the Ellucian Banner Web Tailor module of the Ellucian Banner ERP. “An improper authentication vulnerability (CWE-287) was identified in Banner Web Tailor and Banner Enterprise Identity Services. .
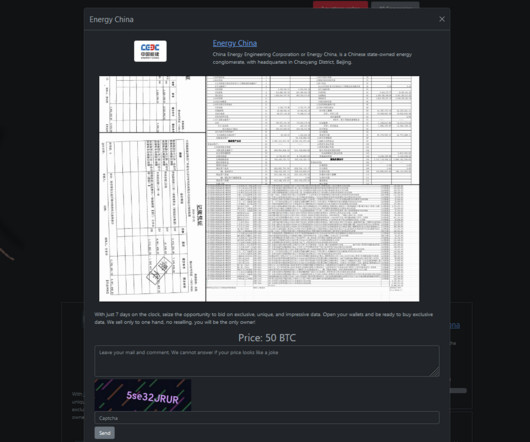
Security Affairs
NOVEMBER 25, 2023
The ransomware gang hit organizations in multiple industries, including the education, healthcare, manufacturing, information technology, and government sectors. The group relied on compromised credentials to authenticate to internal VPN access points. The victims of the group are “targets of opportunity.”

Security Affairs
OCTOBER 12, 2020
The experts discovered how to fully compromise the Apple Distinguished Educators Program via Authentication and bypass authorization and hot to fully compromise the DELMIA Apriso Application via authentication bypass. ” reported the experts.

Security Affairs
JANUARY 13, 2024
An unauthenticated, remote attacker can exploit the vulnerability to conduct a brute force attack in an attempt to identify valid username and password combinations or an authenticated, remote attacker to establish a clientless SSL VPN session with an unauthorized user. Cisco investigated the hacking campaign with the help of Rapid7.
Security Affairs
MAY 3, 2020
ZDNet confirmed the authenticity of the leaked data. Tokopedia is currently investigating the security breach, it notified the users asking them to reset their account passwords.
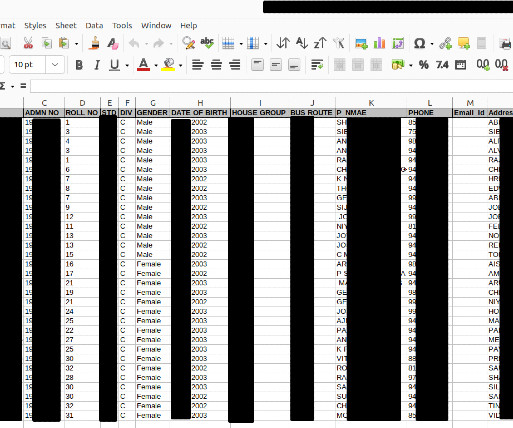
Security Affairs
NOVEMBER 24, 2023
The DigitalOcean storage bucket, containing almost a million sensitive files, was left open to anyone without requiring authentication. Leaking private data on the internet, in this case, poses a grave risk, as most of the leaked files expose minors.

Thales Cloud Protection & Licensing
OCTOBER 4, 2022
Cybersecurity Awareness Month: Resilient Multi-factor Authentication (MFA) and Strong Passwords. Awareness events foster to shape human attitude, enhance a positive culture against cyber threats, and educate businesses and people about protective measures they can take to secure their sensitive personal data: Enable MFA.

Security Affairs
FEBRUARY 10, 2022
Use strong multi-factor authentication methods such as biometrics, physical security tokens, or standalone authentication applications to access online accounts. The FBI recommends mobile carriers take the following precautions: Educate employees and conduct training sessions on SIM swapping. Pierluigi Paganini.
Security Affairs
JANUARY 24, 2020
PoC (Denial-of-Service) for CVE-2020-0609 & CVE-2020-0610 Please use for research and educational purpose only. This vulnerability is pre-authentication and requires no user interaction. link] pic.twitter.com/R43AHUwGV0 — ollypwn (@ollypwn) January 23, 2020. ” reads the advisories published by Microsoft.

Jamf
AUGUST 25, 2022
With Apple School Manager introducing federated authentication with Google Workspace, it is now easier than ever for educators to work with the Apple and Google ecosystems side by side, getting the most out of each. Read on for observations about the power of Google apps on iPad.
Security Affairs
JANUARY 21, 2021
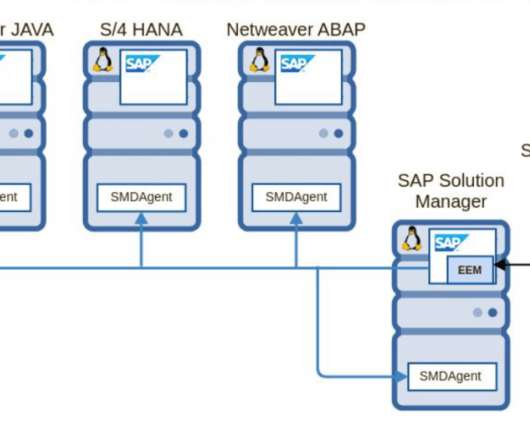
due to Missing Authentication Check does not perform any authentication for a service resulting in complete compromise of all SMDAgents connected to the Solution Manager.” Last week, Dmitry Chastuhin released a PoC exploit code for CVE-2020-6207 for educational purposes. ” reads the advisory.

Security Affairs
APRIL 13, 2023
Successful exploitation can lead to remote, unauthenticated access to Redis and MongoDB instances via crafted authentication requests. ” reads the advisory published by the vendor.
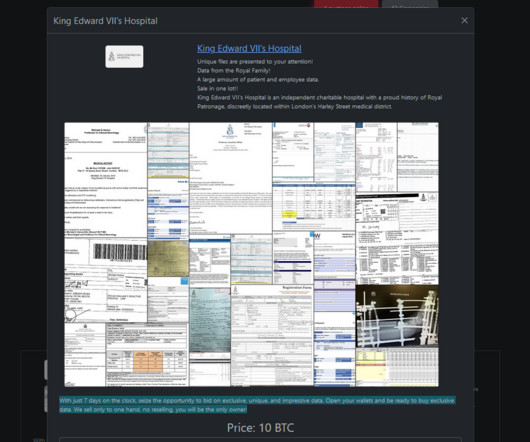
Security Affairs
NOVEMBER 29, 2023
The ransomware gang hit organizations in multiple industries, including the education, healthcare, manufacturing, information technology, and government sectors. The group relied on compromised credentials to authenticate to internal VPN access points. The Rhysida ransomware group has been active since May 2023.
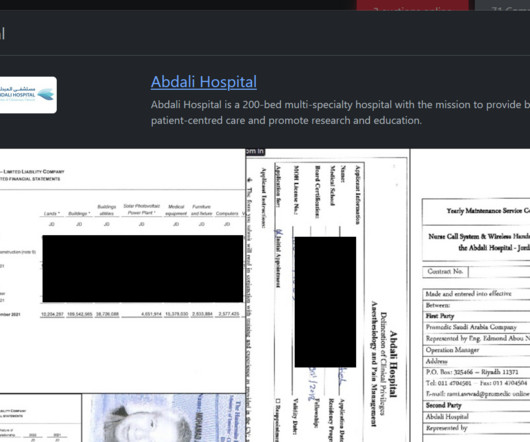
Security Affairs
DECEMBER 26, 2023
The ransomware gang hit organizations in multiple industries, including the education, healthcare, manufacturing, information technology, and government sectors. The group relied on compromised credentials to authenticate to internal VPN access points. The Rhysida ransomware group has been active since May 2023.

Security Affairs
APRIL 4, 2023
Below is the list of flaws exploited by the ransomware gang’s affiliate: CVE-2021-27876 : The communication between a client and an Agent requires successful authentication, which is typically completed over a secure TLS communication. It supports multiple authentication schemes: SHA authentication is one of these.

The Last Watchdog
NOVEMBER 19, 2023
As the companies face nine federal lawsuits for failing to protect customer data, it’s abundantly clear hackers have checkmated multi-factor authentication (MFA). But the coup de gras was how easily they brushed aside the multi-factor authentication protections. How they steamrolled multi-factor authentication is a reason for pause.

Security Affairs
JULY 28, 2020
million $1,200 Minted 5 million $2,500 Styleshare 6 million $2,700 Ggumim 2 million $1,300 Mindful 2 million $1,300 StarTribune 1 million $1,100 ChatBooks 15 million $3,500 The Chronicle Of Higher Education 3 million $1,500 Zoosk 30 million $500. The remaining nine databases were already released by ShinyHunters in the past. Appen.com 5.8
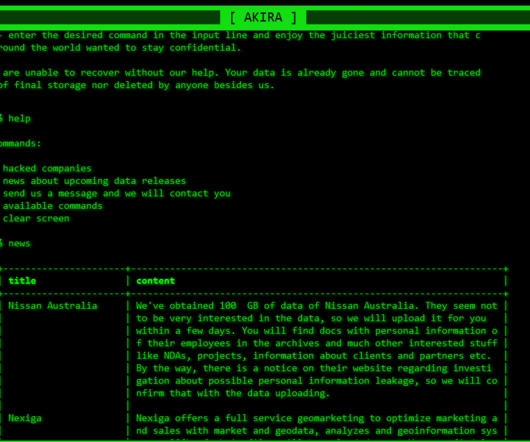
Security Affairs
APRIL 21, 2024
The Akira ransomware has been active since March 2023, the threat actors behind the malware claim to have already hacked multiple organizations in multiple industries, including education, finance, and real estate. Like other ransomware gangs, the group has developed a Linux encryptor to target VMware ESXi servers.

Security Affairs
APRIL 21, 2023
“A vulnerability in the web UI of Cisco IND could allow an authenticated, remote attacker to execute arbitrary commands with administrative privileges on the underlying operating system of an affected device.” ” reads the advisory. “This vulnerability is due to improper input validation when uploading a Device Pack.

Security Affairs
JUNE 2, 2024
OpenAI’s Altman Sidesteps Questions About Governance, Johansson at UN AI Summit Follow me on Twitter: @securityaffairs and Facebook and Mastodon Pierluigi Paganini ( SecurityAffairs – hacking, newsletter)

Security Affairs
DECEMBER 17, 2020
The FBI PIN, Number 20201210-001, was issued on December 10, 2020, and provides details about Doppelpaymer’s criminal activity and the sectors on which the group focuses (Healthcare, Emergency Services, and Educational Institutions). PIN Number 20201210-001. Patch operating systems, software, firmware, and endpoints.

eSecurity Planet
NOVEMBER 6, 2024
They could even conceal dangerous malware in photos or links on secure websites you visit, and a single click can activate the code, even overcoming multifactor authentication. Train Your Admin & Staff Educate personnel on the risks of session hijacking and best practices for prevention to foster a security-conscious culture.

Security Affairs
APRIL 28, 2023
The company also fixed a high-severity post-authentication command injection issue ( CVE-2023-27991 , CVSS score: 8.8) The vulnerability can be exploited by a remote, authenticated attacker to execute some OS commands. ” reads the advisory published by the vendor. affecting some specific firewall versions. through 5.35.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content