New EU Strong Customer Authentication Standards: Implications for Payment Service Providers
Data Matters
SEPTEMBER 18, 2019
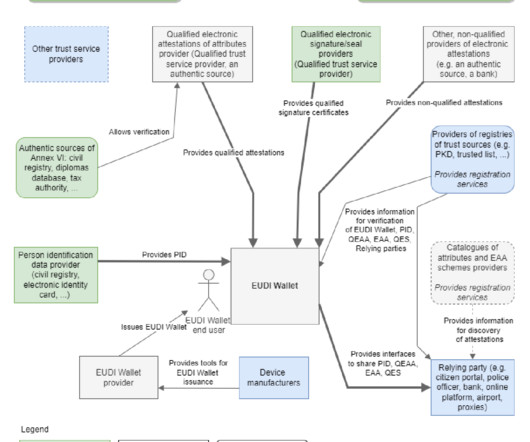
Under the revised Payment Services Directive (2015/2366) (PSD2), the European Banking Authority (EBA) and the European Commission were required to develop and adopt regulatory technical standards on strong customer authentication and common and secure open standards of communication. STRONG CUSTOMER AUTHENTICATION. What is SCA?































Let's personalize your content