eIDAS 2.0 REGULATION WILL CHANGE IDP USE CASES INCLUDING ID CAPTURE IN THE EU
Info Source
JULY 18, 2023
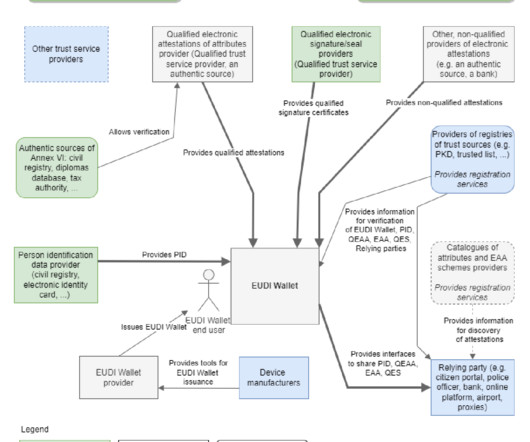
By Petra Beck, Senior Analyst Capture Software, Infosource Key Takeaways The expanded eIDAS (electronic Identification, Authentication and Trust Services) 2.0 One of the four key dimensions of this program is the digitalisation of public services. regulation is entering implementation stage in the EU.













Let's personalize your content