DDoS amplify attack targets Citrix Application Delivery Controllers (ADC)
Security Affairs
DECEMBER 24, 2020
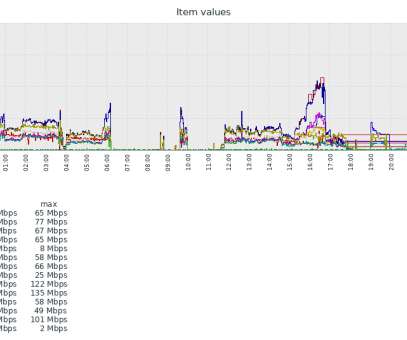
The DTLS protocol is a communications protocol for securing delay-sensitive apps and services that use datagram transport. The attacks began last week, the systems administrator Marco Hofmann first detailed them. I found these source IP addresses of the attackers in my nstraces: 45.200.42.0/24 24 220.167.109.0/24











Let's personalize your content