Russia-linked hackers target Ukrainian military with Infamous Chisel Android malware
Security Affairs
AUGUST 31, 2023
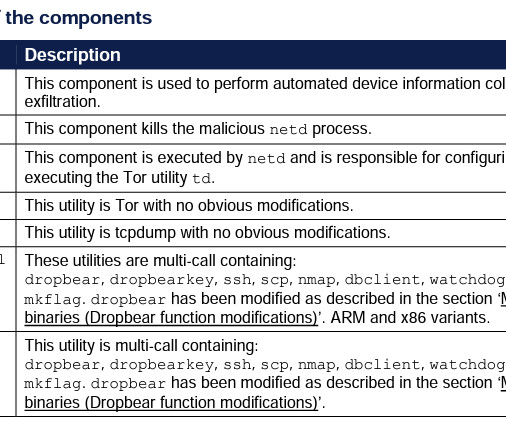
Russia-linked threat actors have been targeting Android devices of the Ukrainian military with a new malware dubbed Infamous Chisel. “The information exfiltrated is a combination of system device information, commercial application information and applications specific to the Ukrainian military. ” concludes the report.





























Let's personalize your content