How to use ChatGPT to summarize a book, article, or research paper
Collaboration 2.0
MARCH 30, 2023
If you're confronted with a long document or a lot of complicated text, here's how to use ChatGPT to summarize the key points. AI chatbots like …
This site uses cookies to improve your experience. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country, we will assume you are from the United States. Select your Cookie Settings or view our Privacy Policy and Terms of Use.
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
Used for the proper function of the website
Used for monitoring website traffic and interactions
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
 Article Related Topics
Article Related Topics 
Collaboration 2.0
MARCH 30, 2023
If you're confronted with a long document or a lot of complicated text, here's how to use ChatGPT to summarize the key points. AI chatbots like …

Collaboration 2.0
OCTOBER 25, 2024
Here's how to transform your writing workflow and turn your Apple Watch into a productivity powerhouse.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

WIRED Threat Level
JUNE 28, 2024
WIRED was able to download stories from publishers like The New York Times and The Atlantic using Poe’s Assistant bot. One expert calls it “prima facie copyright infringement,” which Quora disputes.
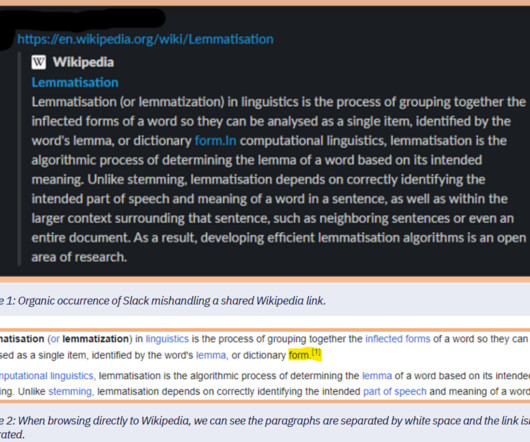
Security Affairs
OCTOBER 30, 2023
The footnote allows to set the stage for a formatting error when the article is shared on Slack. Once certain additional conditions are met – made easy by small grammatical changes to the Wikipedia article, Slack will render a link that is not visible in the original Wikipedia article.
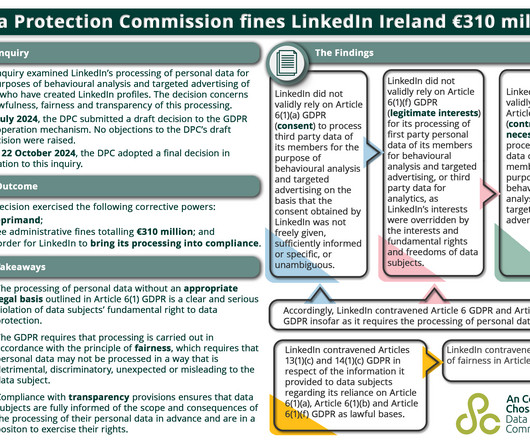
Security Affairs
OCTOBER 25, 2024
The probe claims that LinkedIn infringed GDPR Article 6 GDPR and Article 5(1)(a), Articles 13(1)(c) and 14(1)(c), and Article 5(1)(a). The Irish Agency also mandates LinkedIn to revise its data processing to align with GDPR standards. said DPC Deputy Commissioner Graham Doyle.
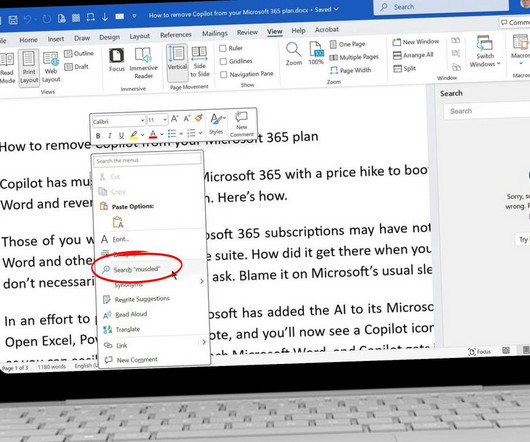
Collaboration 2.0
JANUARY 29, 2025
The defunct feature used to let users search for definitions and online articles about highlighted words and phrases.

Security Affairs
SEPTEMBER 29, 2024
Security Affairs Malware newsletter includes a collection of the best articles and research on malware in the international landscape. Security Affairs Malware newsletter includes a collection of the best articles and research on malware in the international landscape.

Data Matters
DECEMBER 16, 2024
Indeed, by introducing AI literacy as one of the first provisions of the AI Act (Article 4), the EU legislators appear to underscore the significance of this requirement. The post EU AI Act: Are You Prepared for the AI Literacy Principle? appeared first on Data Matters Privacy Blog.

Collaboration 2.0
DECEMBER 21, 2024
The answer is complicated, so in Part I of a two-article analysis, we consulted legal experts to obtain some definitive answers.

Security Affairs
OCTOBER 6, 2024
Security Affairs Malware newsletter includes a collection of the best articles and research on malware in the international landscape. Security Affairs Malware newsletter includes a collection of the best articles and research on malware in the international landscape. Rhadamanthys Stealer Adds Innovative AI Feature in Version 0.7.0
Security Affairs
DECEMBER 2, 2022
This article is going to explore cybersecurity considerations surrounding drone platforms through an initial review of drone market trends, popular drone hacking tools, and general drone hacking techniques that may be used to compromise enterprise drone platforms, including how drone platforms themselves may be used as malicious hacking platforms.

Data Breach Today
DECEMBER 29, 2023
Media Giant Alleges 'Billions of Dollars in Statutory and Actual Damages' The New York Times is suing OpenAI and its chief backer Microsoft for copyright infringement, alleging that OpenAI used without permission "millions" of its copyrighted articles to train the large language models used by ChatGPT and by extension Bing Chat and Copilot.

Security Affairs
JULY 28, 2024
Security Affairs Malware newsletter includes a collection of the best articles and research on malware in the international landscape.

Security Affairs
FEBRUARY 16, 2025
Security Affairs Malware newsletter includes a collection of the best articles and research on malware in the international landscape.

Security Affairs
AUGUST 18, 2024
Security Affairs Malware newsletter includes a collection of the best articles and research on malware in the international landscape.

Security Affairs
FEBRUARY 23, 2025
Security Affairs Malware newsletter includes a collection of the best articles and research on malware in the international landscape. You’ve Got Malware: FINALDRAFT Hides in Your Drafts Telegram Abused as C2 Channel for New Golang Backdoor Infostealing Malware Infections in the U.S.

Security Affairs
JANUARY 26, 2025
Security Affairs Malware newsletter includes a collection of the best articles and research on malware in the international landscape.

Security Affairs
NOVEMBER 21, 2024
Below is the statement provided by the company: “The Softway Medical Group wishes to provide clarifications regarding the recent cyberattack mentioned in certain press articles.

Security Affairs
SEPTEMBER 1, 2024
Security Affairs Malware newsletter includes a collection of the best articles and research on malware in the international landscape.

Security Affairs
SEPTEMBER 22, 2024
Security Affairs Malware newsletter includes a collection of the best articles and research on malware in the international landscape.

Collaboration 2.0
DECEMBER 4, 2024
Using the ElevenLabs Reader app, you can turn articles, webpages, written text, documents, PDFs, and more into AI-powered podcasts. Here's how it differs from NotebookLM.

Security Affairs
SEPTEMBER 16, 2024
” reads The court filing referenced an article published by The Guardian article reporting that Israeli officials seized files from NSO Group’s headquarters. ” reads the article published by the Guardian mentioned in the court filing.
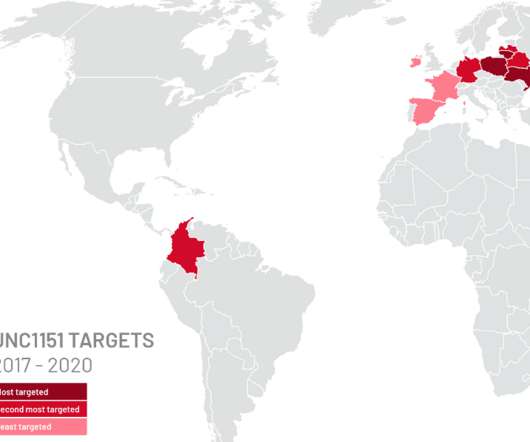
Security Affairs
NOVEMBER 16, 2021
The attackers used to replace existing legitimate articles on the sites with fake content, instead of creating new posts. “ In August 2020, the Ghostwriter campaign spread articles claiming that the protests in Belarus were orchestrated by the U.S. We cannot rule out Russian contributions to either UNC1151 or Ghostwriter.

Collaboration 2.0
FEBRUARY 12, 2025
If you're a budding writer, an advanced author, or somewhere in between, you know that the right tools can help you stay organized and on track to complete that article, memoir, or manuscript.

Security Affairs
AUGUST 11, 2024
Security Affairs Malware newsletter includes a collection of the best articles and research on malware in the international landscape.

Security Affairs
JULY 14, 2024
Security Affairs Malware newsletter includes a collection of the best articles and research on malware in the international landscape.

Collaboration 2.0
NOVEMBER 25, 2024
This article breaks down what happened and shares five hacks to crush your next product launch. The internet has plenty to say about Jaguar's recent colorful rebrand.

Security Affairs
SEPTEMBER 8, 2024
Security Affairs Malware newsletter includes a collection of the best articles and research on malware in the international landscape.

Security Affairs
JULY 21, 2024
Security Affairs Malware newsletter includes a collection of the best articles and research on malware in the international landscape.

Security Affairs
JANUARY 7, 2024
We reached out to the company but did not receive a response before publishing this article. This misconfiguration compromised approximately 230,000 Iranian citizens, exposing their written consent to regulations, as well as passports, IDs, and credit cards. The instance has since been secured and is no longer accessible.

Security Affairs
JULY 7, 2024
Each week, it will feature a collection of the best articles and research on malware. Today marks the launch of the Security Affairs newsletter, specializing in Malware. This newsletter complements the weekly one you already receive.

Security Affairs
SEPTEMBER 15, 2024
Security Affairs Malware newsletter includes a collection of the best articles and research on malware in the international landscape.

Security Affairs
AUGUST 25, 2024
Security Affairs Malware newsletter includes a collection of the best articles and research on malware in the international landscape.

Data Breach Today
JULY 19, 2023
In this article, we'll discuss how to evaluate API security platforms and what factors to consider.

Security Affairs
FEBRUARY 24, 2024
TASS reported that the Russian authorities have opened a criminal case was opened into the incident under Part 4 of Article 274.1 of the local Criminal Code. The local authorities have completed the investigation and sent the evidence to the court for a final judgment.

Security Affairs
FEBRUARY 8, 2024
” reads the new article published by the newspaper. “It ” The newspaper also states that they have submitted the text of the article to Fortinet for verification before publication and the statement that this was a real case that really happened was not objected to. However, the case is not based on research by Fortinet.”

Schneier on Security
NOVEMBER 8, 2024
The Open Source Initiative has published (news article here ) its definition of “open source AI,” and it’s terrible. It allows for secret training data and mechanisms. It allows for development to be done in secret.

Adam Shostack
JANUARY 2, 2025
My latest article at Dark Reading is Microsoft Can Fix Ransomware Tomorrow. My latest at Dark Reading draws attention to how Microsoft can fix ransomware tomorrow. It starts: Recently, I was at a private event on security by design.

Collaboration 2.0
AUGUST 23, 2024
This article provides detailed prompts and tests you can repeat on your favorite AI chatbot to see if it can help you program reliably.

Security Affairs
MAY 26, 2024
CERT-UA published an article that provides more details of the group’s TTPs. UAC-0006 is the most active financially-motivated threat actor targeting Ukraine businesses, has already attempted to steal tens of million hryvnias through mass online theft campaigns in August-October 2023.

Collaboration 2.0
AUGUST 23, 2024
Writing this article about the problem I solved took me a few hours. The actual AI analysis process, from start to finish, took me less than 10 minutes. That's some serious productivity right there.

Security Affairs
JULY 21, 2024
Security Affairs Malware newsletter includes a collection of the best articles and research on malware in the international landscape.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?

Let's personalize your content