New Anti Anti-Money Laundering Services for Crooks
Krebs on Security
AUGUST 13, 2021
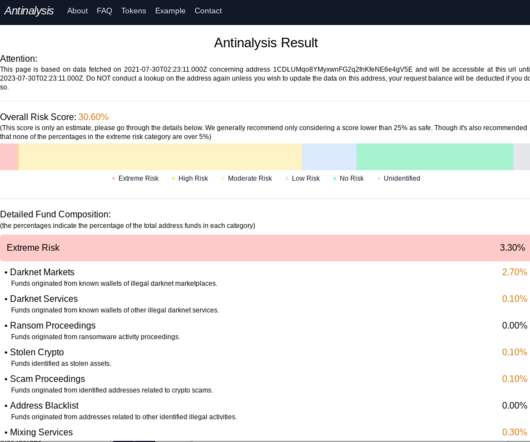
. “Cryptoassets have become an important tool for cybercriminals,” Robinson wrote. “The likes of ransomware and darknet markets rely on payments being made in Bitcoin and other cryptocurrencies. “To date, this type of analysis has been used primarily by regulated financial service providers.”
















Let's personalize your content