MY TAKE: Can ‘Network Traffic Analysis’ cure the security ills of digital transformation?
The Last Watchdog
AUGUST 29, 2018
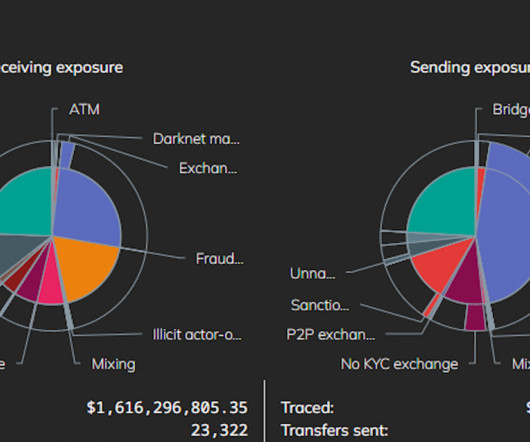
This requires full stream reassembly for content analysis, and then real time transaction analysis, all at speeds of millions of transactions per second.”. By really understanding these relationships, and what represents privileged access and what represents control, we’re able to do much more sophisticated analysis.”.


















































Let's personalize your content