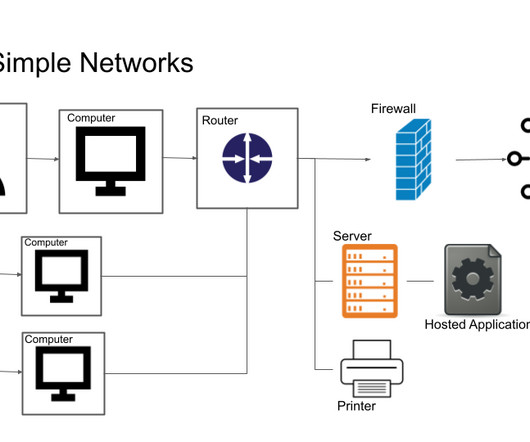
What Is a Host-Based Firewall? Definition & When to Use
eSecurity Planet
FEBRUARY 6, 2024
Logging and reporting: Host-based firewalls keep track of authorized and rejected traffic, which helps with troubleshooting and security analysis. This capability assists post-event analysis, troubleshooting, and keeping an audit record of network activity. Definition & When to Use appeared first on eSecurity Planet.


















































Let's personalize your content