Improve safety using root cause analysis and strengthening information management
OpenText Information Management
NOVEMBER 13, 2024
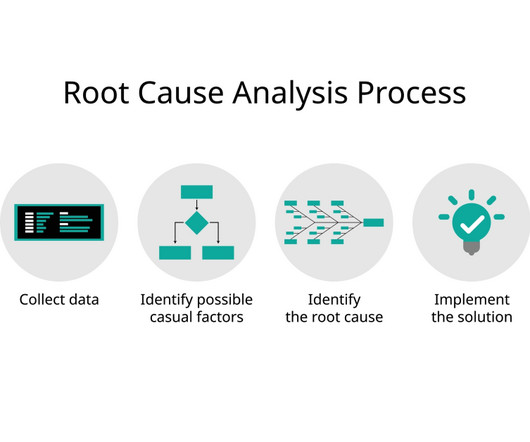
The power of root cause analysis Having worked in the energy industry for two decades and seen accidents and have been exposed to hazards, root causes analysis (RCA) was engrained in me by the organizations I worked for and served. Just as human action needs to be managed to achieve business outcomes, so does information.












































Let's personalize your content