Your PCI-DSS v4.0 Roadmap: Charting a Course of Education, Analysis & System Enhancements
Thales Cloud Protection & Licensing
JULY 4, 2024
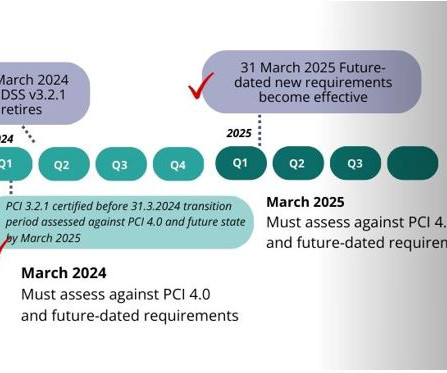
Roadmap: Charting a Course of Education, Analysis & System Enhancements josh.pearson@t… Thu, 07/04/2024 - 07:00 The Payment Card Industry Data Security Standard (PCI-DSS) v4.0 Encryption Shane Tully | Global CISO, A24 More About This Author > The Payment Card Industry Data Security Standard ( PCI-DSS ) v4.0 Your PCI-DSS v4.0








































Let's personalize your content