The Dangerous Weak Link in the US Food Chain
WIRED Threat Level
APRIL 6, 2023
Without an information sharing and analysis center, the country’s food and agriculture sector is uniquely vulnerable to hackers.
This site uses cookies to improve your experience. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country, we will assume you are from the United States. Select your Cookie Settings or view our Privacy Policy and Terms of Use.
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
Used for the proper function of the website
Used for monitoring website traffic and interactions
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.

WIRED Threat Level
APRIL 6, 2023
Without an information sharing and analysis center, the country’s food and agriculture sector is uniquely vulnerable to hackers.
Security Affairs
DECEMBER 12, 2023
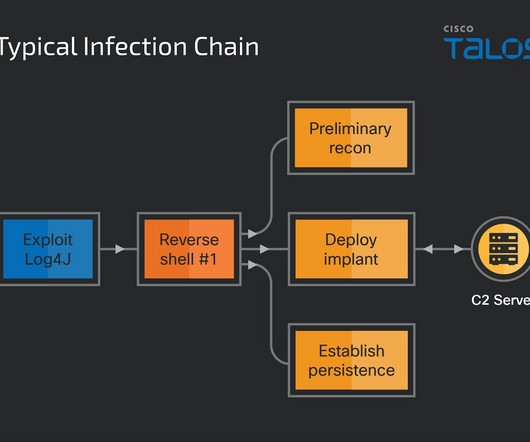
In March, the threat actors hit a South American agricultural organization. ” reads the analysis published by Talos. Talos believes that NineRAT was built around May 2022, but was first spotted on March 2023 as part of Operation Blacksmith.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.
Security Affairs
FEBRUARY 13, 2022
The analysis of the ransomware revealed that it was developed to avoid infecting systems that primarily use Russian or related languages. The experts spotted the BlackByte ransomware while investigating a recent malware incident. ” reads the advisory. ” Follow me on Twitter: @securityaffairs and Facebook.

Security Affairs
JUNE 8, 2019
This week, Chi-en (Ashley) Shen presented at the CONFidence cybersecurity conference held in Poland her analysis on new samples of malware associated with the ICEFOG group. Below the conclusions of the excellent analysis conducted by Shen: ICEFOG is malware shared among Roaming Tiger, APT15, Temp Group A and suspected APT9.

Security Affairs
JULY 15, 2019
This new variant was behind a series of ransomware campaigns beginning in June 2019, including attacks against the City of Edcouch, Texas and the Chilean Ministry of Agriculture.” ” reads the analysis published by CrowdStrike. ” continues the analysis.
Security Affairs
JUNE 15, 2023
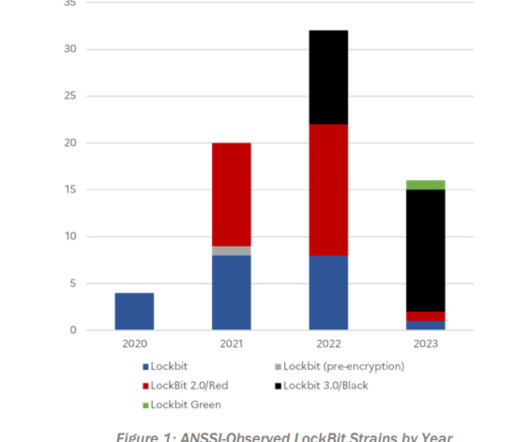
The operation targeted many organizations in critical infrastructure sectors, including financial services, food and agriculture, education, energy, government and emergency services, healthcare, manufacturing, and transportation. organizations since 2020.
Security Affairs
MAY 23, 2023
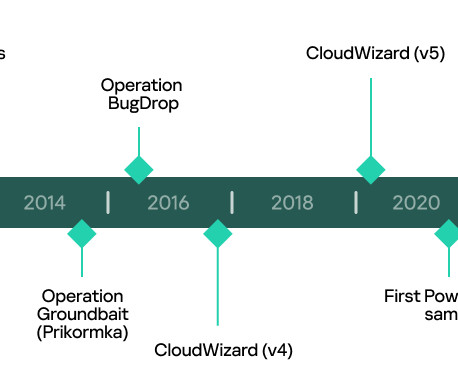
A deeper analysis revealed that the threat actor CloudWizard has been linked to an activity cluster that dates back to May 2016 that was tracked by ESET researchers as Operation Groundbait. Further analysis revealed that the actor behind the above operations has been active since at least 2008. ” We are in the final!

The Security Ledger
DECEMBER 16, 2021
Related Stories Spotlight: How Secrets Sprawl Undermines Software Supply Chain Security Episode 227: What’s Fueling Cyber Attacks on Agriculture ? Episode 218: Denial of Sustenance Attacks -The Cyber Risk To Agriculture. . » Click the icon below to listen. In this episode of the podcast (#232), Tomislav Peri?in

IBM Big Data Hub
DECEMBER 18, 2023
GIS perform spatial analysis of geospatial datasets—consisting of vector data (points, lines and polygons) and raster data (cells with spatial information)—to produce connected visualizations. Agriculture GIS technology makes productive, sustainable farming possible by providing accurate, comprehensive data.

The Texas Record
JUNE 14, 2021
Department of Agriculture, the Fish and Wildlife Service of the U. PW5525-05 SWIMMING POOL REPORTS Swimming pool water quality test and analysis reports. Department of Interior, or other federal or state agencies. Expiration or termination + 3 years. The same goes for the facility’s human visitors.

IBM Big Data Hub
MARCH 25, 2024
” analysis to better understand the likelihood of various climate scenarios and help to draw up mitigation plans to counter extreme weather risks. Investment decision-makers also need weather and climate data so they can use it for better-informed trading in sectors such as energy, agriculture and food.

Schneier on Security
OCTOBER 22, 2019
Still, I like seeing this kind of analysis about security infrastructure. Extending the approach of looking back from 2017 to the larger national economy required the selection of economic sectors best represented by the 169 survey respondents.

RFID Global Solution, Inc.
JULY 15, 2017
The objective of the report is to provide a detailed analysis of the RFID market based on products and tag market based on wafer size, working, frequency, applications, form factor, label type, and region. Animal Tracking/Agriculture. Quantitative Analysis. Detailed analysis of the applications, by label type (for tags).

CILIP
JANUARY 20, 2020
The NUIST major of information management and information systems is based on meteorological data collection and analysis, meteorological information system analysis and design, and meteorological information service. Dr Li Beiqun, President of the University was delighted at the successful outcome.

eSecurity Planet
AUGUST 10, 2023
Incoming data is monitored with automated analysis and graphical visualization tools. Though the ISC’s network of volunteers is full of experts, it’s still a relatively small team with a setup that could lead to inconsistencies in reporting and depth of analysis. Daily diaries detail handler analyses.

Collibra
JANUARY 7, 2025
These limits apply across futures and options contracts, particularly those tied to commodities with significant economic impact, like energy, agriculture and metals. The Commodity Futures Trading Commission (CFTC) establishes position limit requirements to prevent market manipulation, excessive speculation, and systemic risk in U.S.

Collibra
JANUARY 7, 2025
These limits apply across futures and options contracts, particularly those tied to commodities with significant economic impact, like energy, agriculture and metals. The Commodity Futures Trading Commission (CFTC) establishes position limit requirements to prevent market manipulation, excessive speculation, and systemic risk in U.S.

Data Protection Report
APRIL 9, 2024
There are no sector-based criteria for the Commercial Facilities, Dams, or Food and Agriculture sectors, where the entities that would likely impact national security, economic security, or public safety are already identified by size. Generally, CISA anticipates that this analysis should be fairly quick, a matter of hours rather than days.

CGI
NOVEMBER 26, 2018
In addition to government activities, this advanced modeling approach has applications in policy analysis, academic settings and other organizations. AI can perform such analysis in real time, as well as learn from the results of past actions. Traditional modeling has just two dimensions available.

IBM Big Data Hub
FEBRUARY 14, 2024
Voice-based queries use natural language processing (NLP) and sentiment analysis for speech recognition so their conversations can begin immediately. Agricultural machines can engage in autonomous pruning, moving, thinning, seeding and spraying.
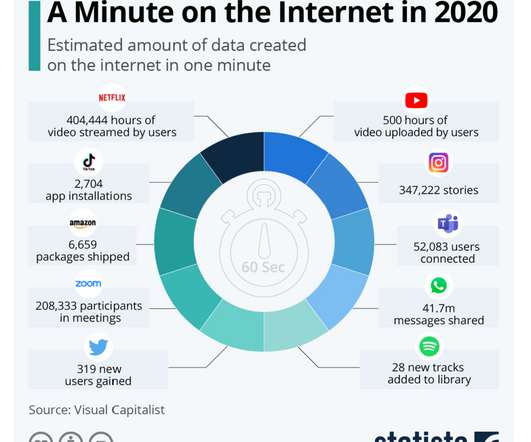
ARMA International
SEPTEMBER 22, 2021
Another example is when sensitive information is removed from transaction data after meeting operational requirements, but the data is kept for analytical processing such as market research and trend analysis. In the Neolithic Revolution, early humans discovered agriculture, which helped establish early civilizations.

Security Affairs
MAY 2, 2024
Pro-Russia hacktivists have been targeting and compromising small-scale Operational Technology (OT) systems in North American and European Water and Wastewater Systems (WWS), Dams, Energy, and Food and Agriculture Sectors.

Security Affairs
MAY 28, 2019
” reads the analysis published by Cisco Talos. “ In April 2019, threat actors launched numerous campaigns aimed at targeting industries such as transportation and logistics, healthcare, import and export, marketing, agriculture, and others. . . ” continues the post.

Archives Blogs
FEBRUARY 18, 2019
Department of Agriculture, where he was involved with research related to black farmers. His first book, published shortly after joining the NAACP, was The Negro Faces America , a progressive analysis of race relations in the United States. Between 1938 and 1944, Holsey was also on loan from the institute to the U.
Security Affairs
JUNE 1, 2021
“The White House has offered assistance to JBS and our team at the Department of Agriculture have spoken to their leadership several times in the last day,” Jean-Pierre said. Department of Agriculture. Analysis observed that U.S. The risk is that the U.S.

IBM Big Data Hub
FEBRUARY 20, 2024
Parts of Africa will be especially vulnerable, with agricultural yields declining by as much as 50% in some areas. The IPCC projects that water available for human use will continue to decline in North America, while water security will be at risk in Africa, Asia and South America.

Data Matters
MARCH 21, 2022
The reporting requirements will cover multiple sectors of the economy, including chemical industry entities, commercial facilities, communications sector entities, critical manufacturing, dams, financial services entities, food and agriculture sector entities, healthcare entities, information technology, energy, and transportation.

IBM Big Data Hub
FEBRUARY 8, 2024
To track the results of such efforts, including energy efficiency and emissions reductions, GPT Group deploys an SaaS tool that consolidates enterprise ESG data for analysis and reporting. And, in the 19th century, settlers in the Americas used windmills to pump water for agriculture.

IT Governance
DECEMBER 11, 2023
At the end of each month, these incidents – and any others that we find – will be used to inform our monthly analysis of data breaches and cyber attacks. Source (New) Agriculture USA Yes Unknown Precision Technologies Group – Holroyd Source (New) Engineering UK Yes Unknown A.G.

IT Governance
FEBRUARY 21, 2024
At the end of each month, these incidents – and any others that we find – will be used to inform our monthly analysis of data breaches and cyber attacks. 402,437,094 known records breached in 240 publicly disclosed incidents Welcome to this week’s global round-up of the biggest and most interesting news stories.

IT Governance
MARCH 11, 2024
At the end of each month, these incidents – and any others that we find – will be used to inform our monthly analysis of data breaches and cyber attacks. 66,702,148 known records breached in 103 newly disclosed incidents Welcome to this week’s global round-up of the biggest and most interesting news stories.

IT Governance
JULY 1, 2020
The Maine Information and Analysis Center breached in ‘Blue Leaks’ hack (unknown). Manitoba Agricultural Services Corporation is notifying clients of a privacy breach (134). Jamesville-DeWitt High School students said obscene messages as email listserv breached (unknown).

Data Protection Report
DECEMBER 17, 2020
The Data Strategy proposed the establishment of nine common European data spaces for data sharing and pooling, including health, mobility, manufacturing, financial services, energy, and agriculture. Such bodies could also support the management of consents.

IT Governance
DECEMBER 5, 2023
At the end of each month, these incidents – and any others that we find – will be used to inform our monthly analysis of data breaches and cyber attacks. Welcome to this week’s round-up of the biggest and most interesting news stories.

DLA Piper Privacy Matters
OCTOBER 1, 2019
The benefits are enormous, as digital communication facilitates exchanges and searches, and enhances consumer choices not only in purchasing consumer goods, but also in finance, healthcare, and producing industries from manufacture to agriculture. were not yet developed.

IT Governance
FEBRUARY 14, 2024
At the end of each month, these incidents – and any others that we find – will be used to inform our monthly analysis of data breaches and cyber attacks. 92,391,296 known records breached in 222 publicly disclosed incidents Welcome to this week’s global round-up of the biggest and most interesting news stories. GB Signature Performance, Inc.

IT Governance
APRIL 9, 2024
At the end of each month, these incidents – and any others that we find – will be used to inform our monthly analysis of data breaches and cyber attacks. 67,273,297 known records breached in 130 newly disclosed incidents Welcome to this week’s global round-up of the biggest and most interesting news stories.

IT Governance
APRIL 22, 2024
At the end of each month, these incidents – and any others that we find – will be used to inform our monthly analysis of data breaches and cyber attacks. 16,482,365 known records breached in 240 newly disclosed incidents Welcome to this week’s global round-up of the biggest and most interesting news stories.

IBM Big Data Hub
NOVEMBER 16, 2023
We will also add more advanced courses that take a deeper look at how data analysis and visualization skills can be applied to practical sustainability use cases, such as examining energy consumption in a community. The courses also provide instruction in data analytics contextualized around sustainability use cases.
Collibra
SEPTEMBER 6, 2024
billion in charitable contributions and over a million hours of annual volunteer community service — TELUS operates in verticals such as communications, online security, smart home security, health and agriculture. Alongside its motto of “giving back where we live” — including $1.3

IT Governance
JANUARY 3, 2024
At the end of each month, these incidents – and any others that we find – will be used to inform our monthly analysis of data breaches and cyber attacks. Following our Christmas break, we’re rounding up two weeks’ worth of the biggest and most interesting news stories.

IT Governance
FEBRUARY 27, 2024
At the end of each month, these incidents – and any others that we find – will be used to inform our monthly analysis of data breaches and cyber attacks. 18,267,244 known records breached in 94 newly disclosed incidents Welcome to this week’s global round-up of the biggest and most interesting news stories. million individuals in its systems.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content