Don’t trust links with known domains: BMW affected by redirect vulnerability
Security Affairs
JANUARY 3, 2024
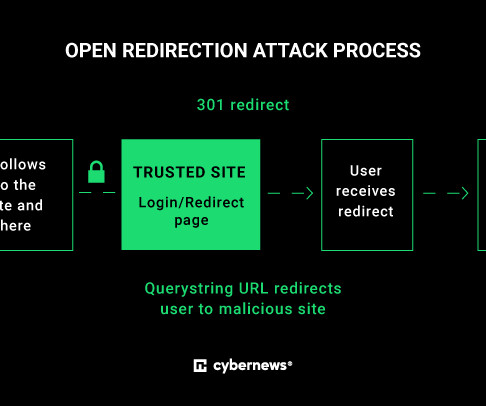
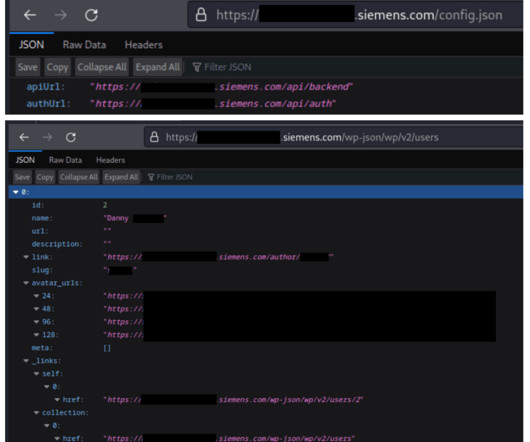
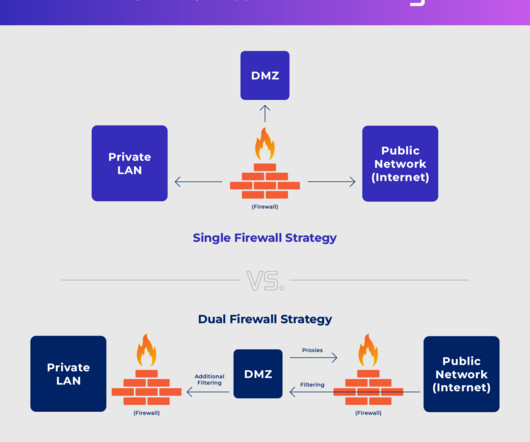
They were used to access the internal workplace systems for BMW dealers and could have been useful to attackers for spear-phishing campaigns or malware distribution. SAP redirect vulnerability is a security issue that affects web application servers for SAP products (SAP NetWeaver Application Server Java).

























Let's personalize your content