What is Tailgating? Definition, Examples & Prevention
IT Governance
JULY 27, 2023
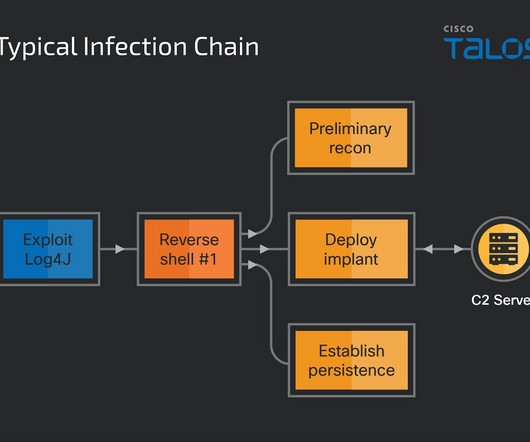
Fraudsters have countless tricks up their sleeves to bypass security measures and access sensitive information. In most cases, this refers to cyber crime, but scammers might also gain physical access to their premises in tailgating attacks. A tailgater here is someone who stays close to a person as they enter or exit a building.













































Let's personalize your content