This Identity Management Day, Go BIG or Go HOME!
Thales Cloud Protection & Licensing
APRIL 11, 2023
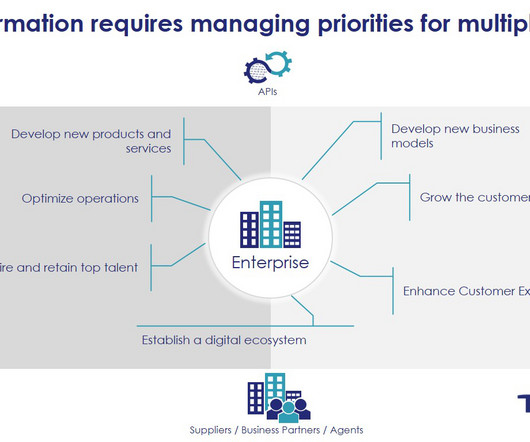
madhav Wed, 04/12/2023 - 06:11 Identity and Access Management (IAM) has evolved significantly over the past decade. CIAM (Customer Identity & Access Management) has recently seen phenomenal growth of late. Cloud-based Access Management Steps Up! IAM is no longer just a means to be compliance- and audit-friendly.
















































Let's personalize your content