Threat Group TeamTNT Returns with New Cloud Attacks
eSecurity Planet
SEPTEMBER 21, 2022
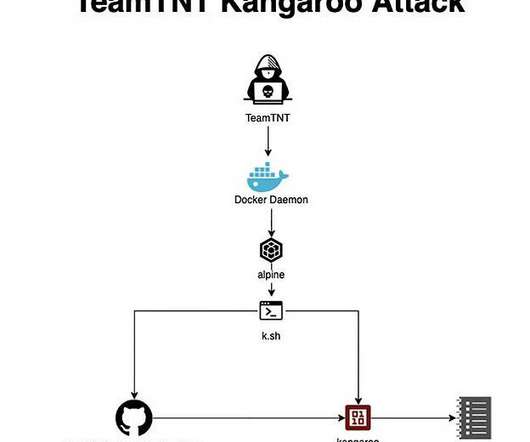
A retired threat actor has returned with new attacks aimed at the cloud, containers – and encryption keys. However, the researchers are convinced the threat actor is back, as their honeypots identified TeamTNT signatures and tools in a series of three attacks during the first week of September. format(len(targets)).


















Let's personalize your content