Vulnerability Recap 9/16/24 – Critical Endpoint Flaws Emerged
eSecurity Planet
SEPTEMBER 16, 2024
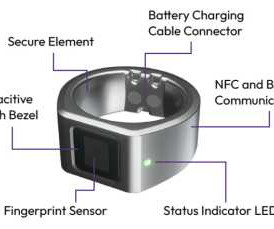
To protect your devices, update and patch your software frequently, use strong passwords, install intrusion detection systems, and watch for any suspicious activity. September 9, 2024 RAMBO Attack Exploits Radio Signals to Steal Sensitive Data Type of vulnerability: Side-channel attack.













Let's personalize your content