Operation Cronos: law enforcement disrupted the LockBit operation
Security Affairs
FEBRUARY 19, 2024
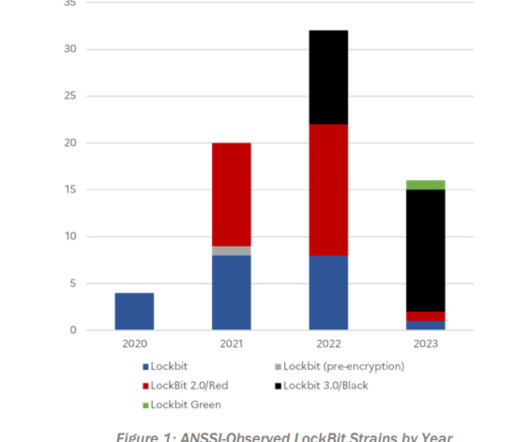
In 2022, LockBit was one of the most active ransomware groups, and its prevalence continued into 2023. Lockbit ransomware group administrative staff has confirmed with us their websites have been seized.

















Let's personalize your content