Weakness at the Network Edge: Mandiant Examines 2022’s Zero-Day Exploits
eSecurity Planet
MARCH 27, 2023
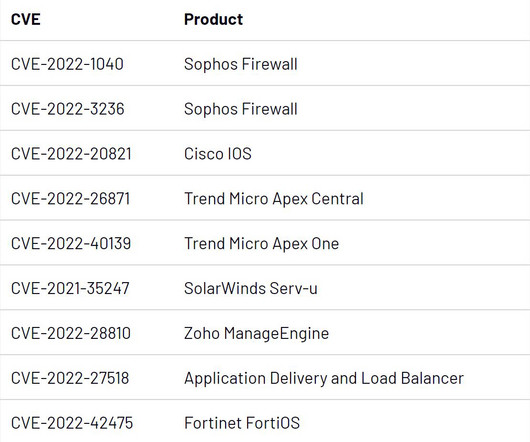
Mandiant tracked 55 zero-day vulnerabilities that were actively exploited in 2022. Overall, the proportion of financially motivated zero-day exploitation decreased in 2022. Far more of the 16 cases with a clear motive were state-sponsored – 13 of the zero-days tracked in 2022 appear to have been leveraged by cyber espionage groups.














Let's personalize your content