Five Steps to Win the Battle Against Information Chaos in 2021
AIIM
APRIL 15, 2021
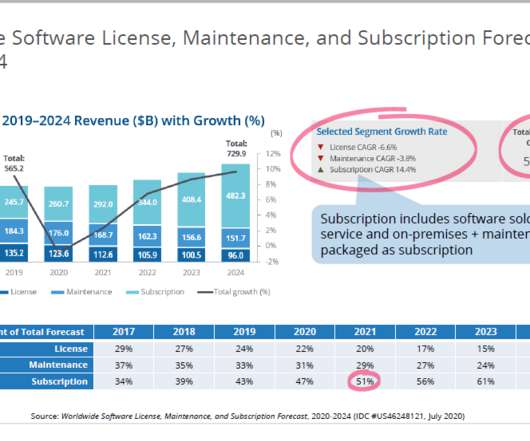
Here's a look at how the AIIM Community self-assessed on how well the strategies for business and technology align in their organization. For fun and visual effect, we've created this 2021 Informational Professionals' report card to present the results. How to Deal with Information Chaos. Step 4: Pick Where to Start.













































Let's personalize your content