FBI training document shows lawful access to multiple encrypted messaging apps
Security Affairs
DECEMBER 1, 2021
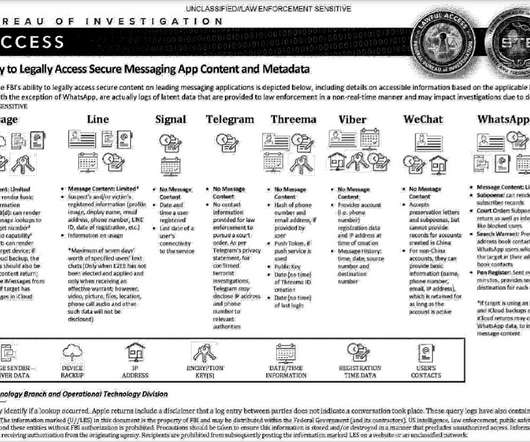
Which are the most secure encrypted messaging apps? An FBI document shows what data can be obtained from them. The Record shared an FBI training document that reveals the surveillance capabilities of the US law enforcement detailing which data can be extracted from encrypted messaging apps. ” reads the document.














































Let's personalize your content