New IRS Site Could Make it Easy for Thieves to Intercept Some Stimulus Payments
Krebs on Security
APRIL 10, 2020
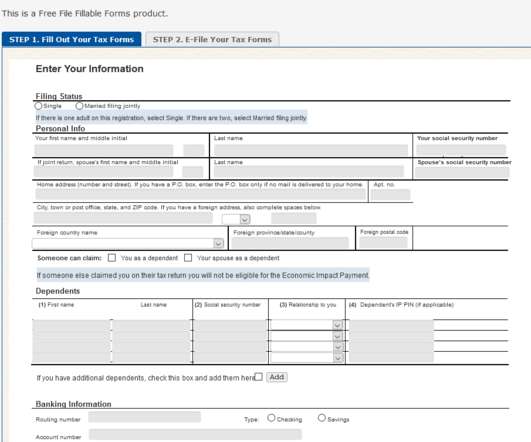
Most people who who filed a tax return in 2018 and/or 2019 and provided their bank account information for a debit or credit should soon see an Economic Impact Payment direct-deposited into their bank accounts. Likewise, people drawing Social Security payments from the government will receive stimulus payments the same way.






































Let's personalize your content