Siemens Metaverse exposes sensitive corporate data
Security Affairs
APRIL 15, 2023
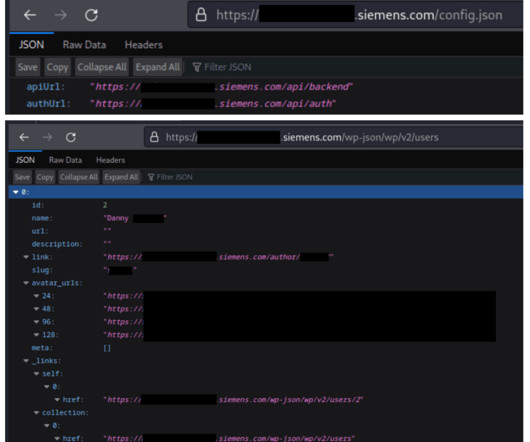
The WordPress sets only exposed user names and avatar pictures, but all four Siemens WordPress-based subdomains were vulnerable to a flaw that WordPress itself fixed in 2017, leaving researchers wondering whether there are more severe vulnerabilities on these sites. There are a lot of opportunities for threat actors here.
















Let's personalize your content