Russia-linked APT28 and crooks are still using the Moobot botnet
Security Affairs
MAY 3, 2024
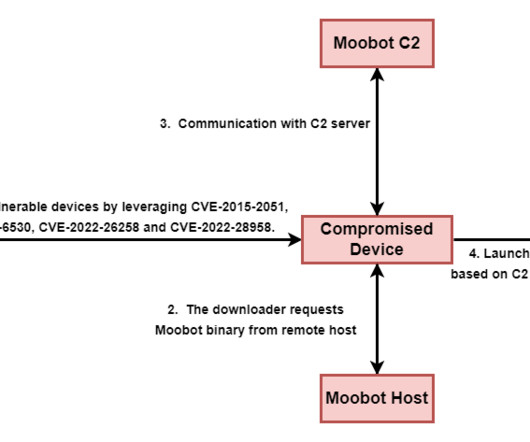
The Moobot botnet has been active since at least 2016, it also includes other routers and virtual private servers (VPS). The threat actors used the botnet harvest credentials, collect NTLMv2 digests, proxy network traffic, and host spear-phishing landing pages and custom tools. ” reported Trend Micro. ” reported Trend Micro.









Let's personalize your content