MY TAKE: Poorly protected local government networks cast shadow on midterm elections
The Last Watchdog
SEPTEMBER 14, 2018
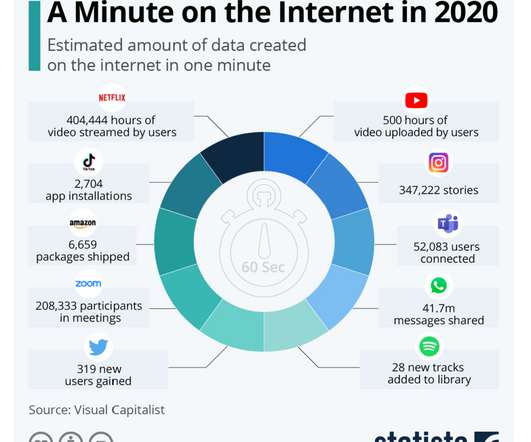
It’s easy to think of it as a problem the federal government must address or something that enterprises deal with, but cybersecurity has to be addressed closer to home, as well. His company supplies a co-managed SIEM service to mid-sized and large enterprises, including local government agencies. During 2016, 39 states were hacked.














Let's personalize your content