Russia-linked APT8 exploited Outlook zero-day to target European NATO members
Security Affairs
DECEMBER 7, 2023
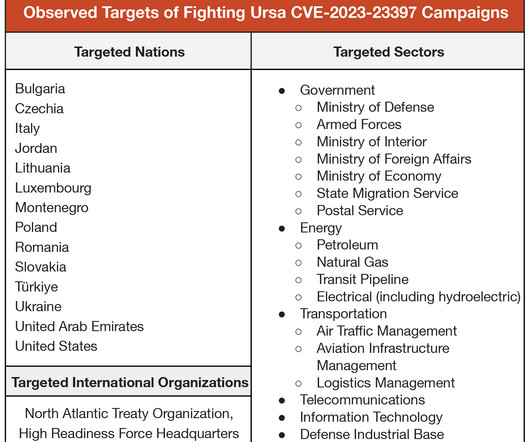
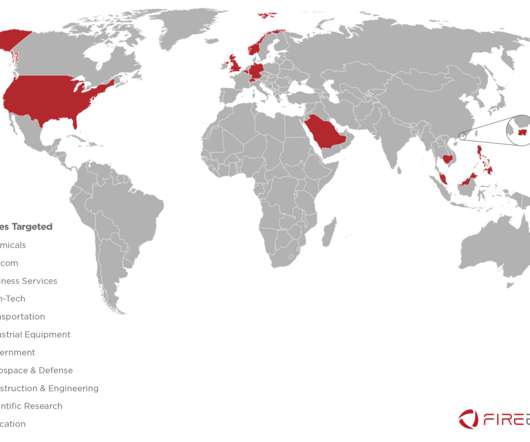
Over the past 20 months, the group targeted at least 30 organizations within 14 nations that are probably of strategic intelligence significance to the Russian government and its military. The group was involved also in the string of attacks that targeted 2016 Presidential election.




























Let's personalize your content