Russia-linked APT28 and crooks are still using the Moobot botnet
Security Affairs
MAY 3, 2024
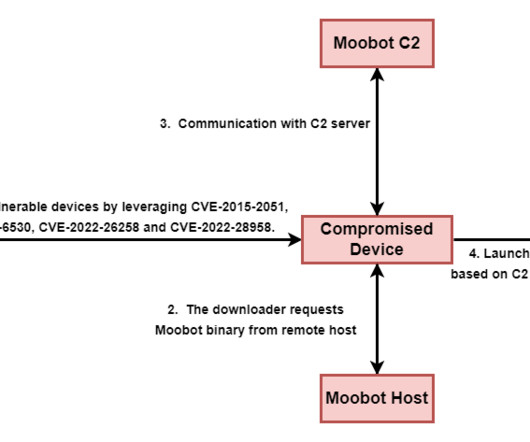
The Moobot botnet has been active since at least 2016, it also includes other routers and virtual private servers (VPS). Pawn Storm most likely easily brute forced the credentials of the backdoored SSH servers and thus gained access to a pool of EdgeRouter devices they could abuse for various purposes.”




















Let's personalize your content