Operation Blacksmith: Lazarus exploits Log4j flaws to deploy DLang malware
Security Affairs
DECEMBER 12, 2023
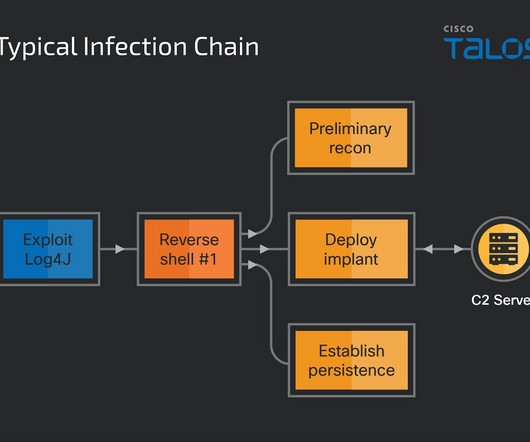
North Korea-linked APT group Lazarus was spotted exploiting Log4j vulnerabilities to deploy previously undocumented remote access trojans. The North Korea-linked APT group Lazarus is behind a new hacking campaign that exploits Log4j vulnerabilities to deploy previously undocumented remote access trojans (RATs).






































Let's personalize your content