From iPhone to NT AUTHORITYSYSTEM – exploit ‘Printconfig’ dll with a real-world example
Security Affairs
DECEMBER 15, 2019
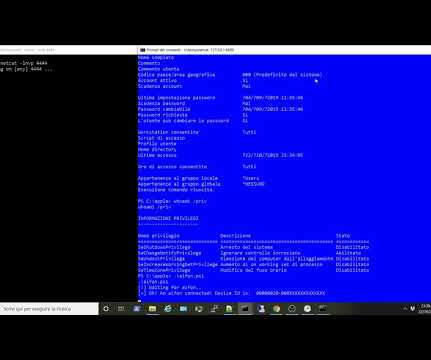
From iPhone to NT AUTHORITYSYSTEM – As promised in my previous post , I will show you how to exploit the “Printconfig” dll with a real world example. of iTunes but did not fix the issue 12th December 2019: still no answer, the post has been published. He likes writing and speaking about IT security and bug hunting.

















Let's personalize your content