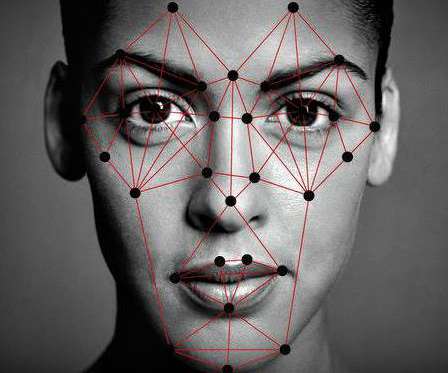
Tech firms suspend use of ‘biased’ facial recognition technology
Security Affairs
JUNE 14, 2020
“The bottom line for us is to protect the human rights of people as this technology is deployed,” Below the video interviews published by The Washington Post: This week Amazon announced a one-year moratorium to ban the sale of facial recognition technology to police departments. SecurityAffairs – facial recognition, privacy).














Let's personalize your content