CIRWA Project tracks ransomware attacks on critical infrastructure
Security Affairs
SEPTEMBER 14, 2020
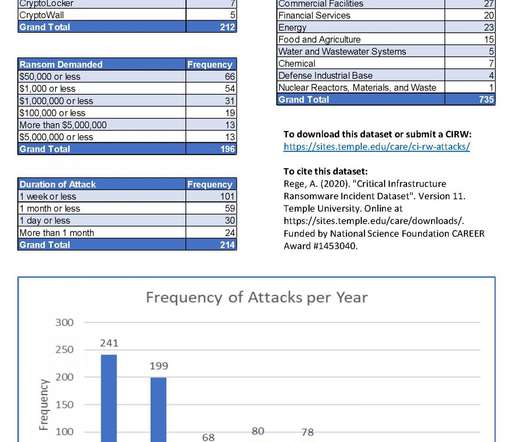
According to the summary findings related to the period 2013-2020, the most targeted critical infrastructures are government facilities, followed by education and healthcare. Data collected by the researchers are very interesting and very useful for future research projects on the security of the critical infrastructure.














Let's personalize your content