Iran-linked APT35 accidentally exposed 40 GB associated with their operations
Security Affairs
JULY 17, 2020
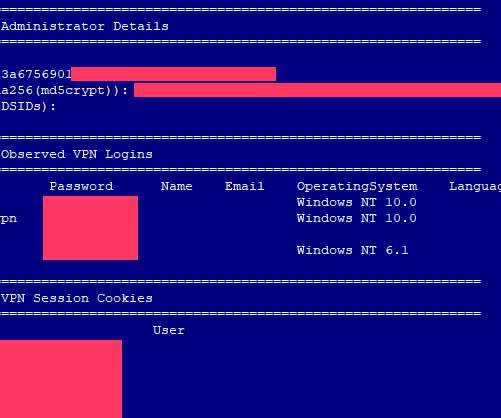
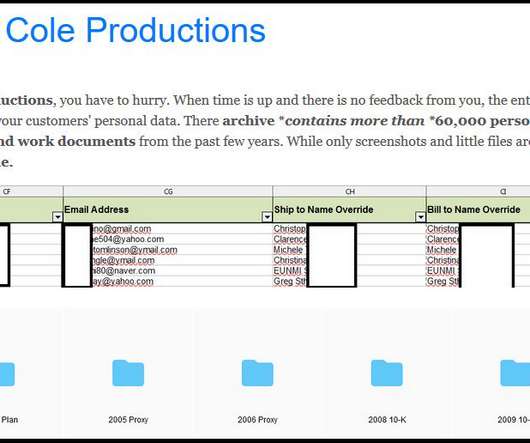
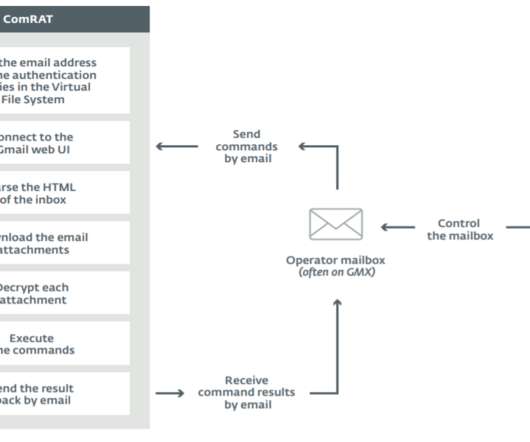
Iran-linked Charming Kitten group, (aka APT35 , Phosphorus , Newscaster , and Ajax Security Team) made the headlines in 2014 when experts at iSight issued a report describing the most elaborate net-based spying campaign organized by Iranian hackers using social media. Copyright (C) 2014 Media.net Advertising FZ-LLC All Rights Reserved -->.
















Let's personalize your content