Symantec uncovered the link between China-Linked Thrip and Billbug groups
Security Affairs
SEPTEMBER 9, 2019
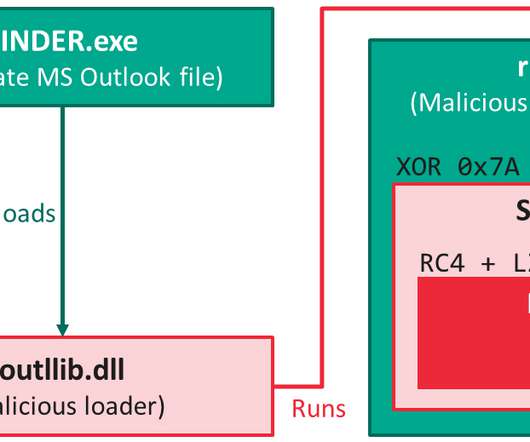
Experts at Symantec first exposed the activity of the Chinese-linked APT Thrip in 2018, now the security firm confirms that cyber espionage group has continued to carry out attacks in South East Asia. The Thrip group has been active since 2013, but this is the first time Symantec publicly shared details of its activities.












Let's personalize your content