Who Stole 3.6M Tax Records from South Carolina?
Krebs on Security
APRIL 16, 2024
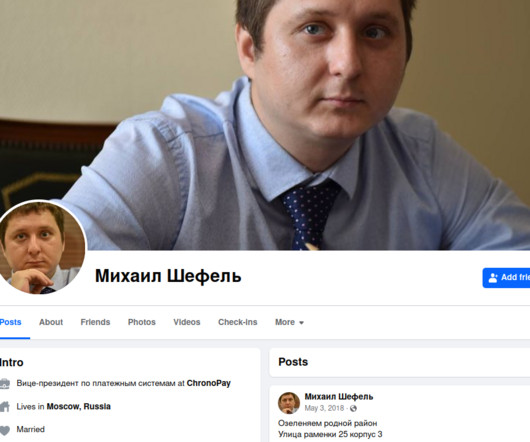
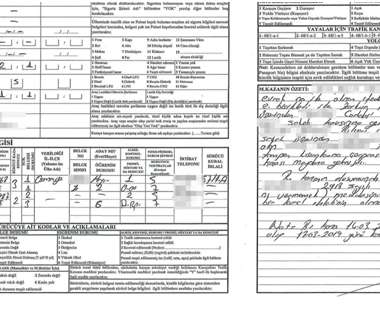
For nearly a dozen years, residents of South Carolina have been kept in the dark by state and federal investigators over who was responsible for hacking into the state’s revenue department in 2012 and stealing tax and bank account information for 3.6 13, 2012, after a state IT contractor clicked a malicious link in an email.










































Let's personalize your content