North Korea-linked APT37 exploited IE zero-day in a recent attack
Security Affairs
OCTOBER 19, 2024
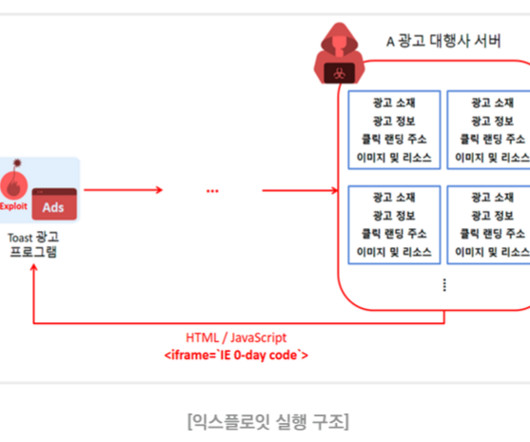
“This attack requires an authenticated client to click a link in order for an unauthenticated attacker to initiate remote code execution.” Cyber attacks conducted by the APT37 group mainly targeted government, defense, military, and media organizations in South Korea.













Let's personalize your content