Mitsubishi Electric discloses data breach, media blame China-linked APT
Security Affairs
JANUARY 20, 2020
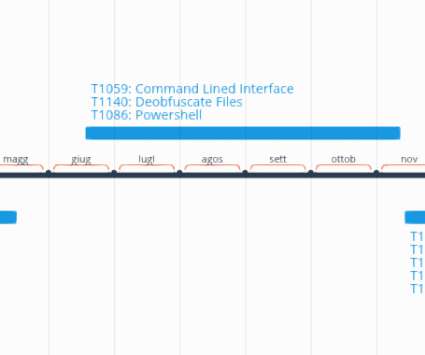
The breach was detected almost eight months ago, on June 28, 2019, with the delay being attributed to the increased complexity of the investigation caused by the attackers deleting activity logs. The intrusion took place on June 28, 2019, and the company launched an investigation in September 2019.
















Let's personalize your content