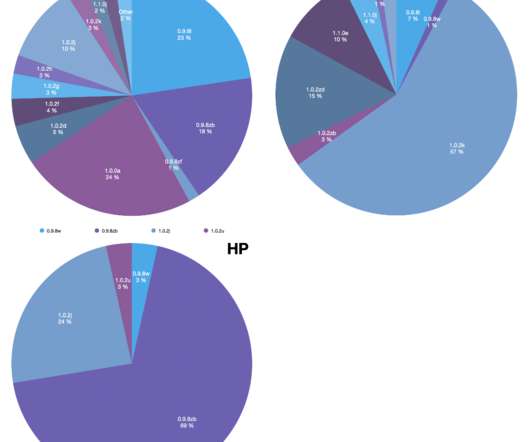
The analysis of the code reuse revealed many links between North Korea malware
Security Affairs
AUGUST 10, 2018
The experts focused their analysis on the code reuse, past investigations revealed that some APT groups share portions of code and command and control infrastructure for their malware. In defining similarities, we take into account only unique code connections, and disregard common code or libraries. ” states the report.


















Let's personalize your content