Google Stored G Suite Passwords in Plaintext Since 2005
Threatpost
MAY 22, 2019
Google said it had stored G Suite enterprise users' passwords in plain text since 2005 marking a giant security faux pas.
This site uses cookies to improve your experience. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country, we will assume you are from the United States. Select your Cookie Settings or view our Privacy Policy and Terms of Use.
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
Used for the proper function of the website
Used for monitoring website traffic and interactions
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
 2005 Related Topics
2005 Related Topics 
WIRED Threat Level
MAY 21, 2019
On the heels of embarrassing disclosures from Facebook and Twitter, Google reveals its own password bugs—one of which lasted 14 years.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Data Breach Today
NOVEMBER 15, 2017
The Final FFIEC Guidance has been issued and its main intent is to reinforce the 2005 Guidance's risk management framework and update the Agencies' expectations regarding customer authentication, layered security, or other controls in the increasingly hostile online environment.

Krebs on Security
NOVEMBER 8, 2020
In 2005, AOL won a $12.8 Hawke had reportedly bragged about the money he earned from spam, but told friends he didn’t trust banks and decided to convert his earnings into gold and platinum bars. That sparked rumors that he had possibly buried his ill-gotten gains on his parents’ Massachusetts property.

Krebs on Security
JUNE 22, 2022
Stanx said he was a longtime member of several major forums, including the Russian hacker forum Antichat (since 2005), and the Russian crime forum Exploit (since April 2013). In an early post to Antichat in January 2005, Stanx disclosed that he is from Omsk , a large city in the Siberian region of Russia.

Data Breach Today
FEBRUARY 9, 2023
CEO Change Marks First Time Since 2005 Someone Other Than Udi Mokady Is In Charge CyberArk will promote Matt Cohen, 47, to CEO on April 3.

ChiefTech
MAY 23, 2012
I wrote this in June 2005. The history of intranets is one of a slow burn of adoption (or innovation, if you like). But the pace of technology change is increasing , email is being challenged. is it time now to dust off the intranet imperative and think about about where we go next? What exactly is an intranet?

Data Breach Today
NOVEMBER 23, 2022
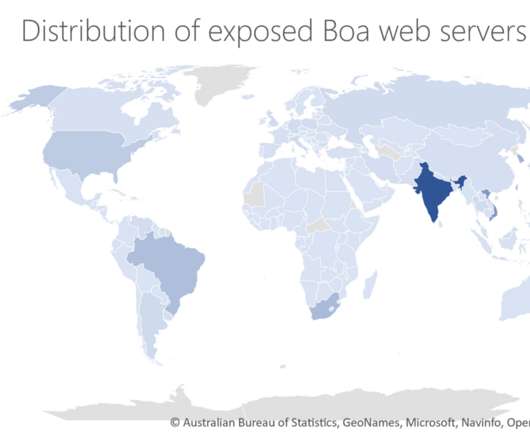
Attackers targeted Boa servers, which were discontinued in 2005, to compromise Tata and other critical infrastructure organizations around the world.

Krebs on Security
MAY 4, 2023
Launched in 2005, Try2Check soon was processing more than a million card-checking transactions per month — charging 20 cents per transaction. ” In February 2005, Nordex posted to Mazafaka that he was in the market for hacked bank accounts, and offered 50 percent of the take. Denis Kulkov, a.k.a. Image: USDOJ.

Krebs on Security
SEPTEMBER 1, 2021
An ad circa 2005 for A311 Death, a powerful banking trojan authored by “Corpse,” the administrator of the early Russian hacking clique Prodexteam. Image: Google Translate via Archive.org.
Krebs on Security
JUNE 28, 2022
ru’s original WHOIS records, which shows it was assigned in 2005 to a “private person” who used the email address lycefer@gmail.com. ru)was registered in 2005 to two men, one of whom was named Dmitry Sergeevich Starovikov. And maybe that was the point. and starovikov[.]com.

The Last Watchdog
OCTOBER 18, 2023
ABE has undergone significant theoretical advancements since 2005. “You can still get useful information from the image, but if you don’t have the correct key, you won’t be able to decrypt certain attributes, such as a face or a license plate number.” Versatile benefits It’s taken a while to get here.

Security Affairs
NOVEMBER 27, 2020
The hackers accessed company file servers that contained information about current and former employees from 2005 to 2020 and their beneficiaries and dependents. The investigation conducted by Canon found evidence of unauthorized accesses on its network between July 20 and August 6. ” reads the statement.

Archives Blogs
OCTOBER 18, 2017
We are pleased to announce that after a significant transfer of records from the Revenue Services Department, the Archives can now make available property tax records up to 2005. 1978-1990 and 1992-2005: Property tax statements: series COV-S289. Map of assessment wards in the Municipality of Point Grey, with proposed changes, ~1927.

KnowBe4
NOVEMBER 21, 2022
Then, in 2005 the clever people at the National Retail Federation decided that an online frenzy of shopping was needed the Monday after Thanksgiving. People arrived at the shops the night before waiting in line for the doors to open. We know this Monday as Cyber Monday.
Krebs on Security
JANUARY 8, 2024
From January 2005 to April 2013, there were two primary administrators of the cybercrime forum Spamdot (a.k.a From one of his ads in 2005: Domains For Projects Advertised By Spam I can register bulletproof domains for sites and projects advertised by spam(of course they must be legal). w s, icamis[.]ru ru , and icamis[.]biz.

Dark Reading
JANUARY 25, 2023
Zacks Elite sign-ups for the period 1999–2005 were accessed, including name, address, email address, phone number, and the password associated with Zacks.com.
Security Affairs
MAY 31, 2021
The feature was first introduced in 2005 with the x64 editions of Windows XP and Windows Server 2003 Service Pack 1. Kento published technical details of its attack in a blog post and also released proof-of-concept (PoC) code for his attack.
Security Affairs
APRIL 19, 2020
” Webkinz were originally released by the Canadian toy company Ganz on April 29, 2005. Webkinz are stuffed animals that have a playable online counterpart, www.webkinz.com, in “Webkinz World.”
Security Affairs
JULY 24, 2020
It was formed in 2005 in response to European Union requirements to separate the natural monopoly of infrastructure management from the competitive operations of running train services. The company has over 13,000 employees for a revenue of around $8 Billion.

John Battelle's Searchblog
JANUARY 9, 2012
2005 Predictions. 2005 How I Did. Predictions 2010. 2010: How I Did. 2009 Predictions. 2009 How I Did. 2008 Predictions. 2008 How I Did. 2007 Predictions. 2007 How I Did. 2006 Predictions. 2006 How I Did. 2004 Predictions. 2004 How I Did.

Security Affairs
MAY 2, 2019
The good news is that most recent versions of SAP software are configured by default to drop unauthorized connections, Since 2005, SAP is providing instructions on how to configure an ACL for the Message Server. Experts pointed out that the problem could impact many SAP products, including S/4HANA and NetWeaver Application Server (AS).

Security Affairs
APRIL 25, 2022
Stuxnet is a malicious computer worm developed to target SCADA systems that were first uncovered in 2010, but researchers believe its development began at least in 2005. . The virus was developed by the US and Israel to interfere with the nuclear enrichment program conducted by Iran in the plant of Natanz.

Hunton Privacy
JUNE 13, 2019
The adaption of French law to the new EU data protection framework was conducted in various stages: The French Data Protection Act of January 6, 1978, was first amended by a law dated June 20, 2018, while its implementing Decree of October 20, 2005, was amended by a Decree of August 1, 2018.

The Last Watchdog
MARCH 9, 2020
Security information and event management systems — SIEMs — have been around since 2005, but their time may have come at last. Related: Digital Transformation gives SIEMs a second wind After an initial failure to live up to their overhyped potential, SIEMs are perfectly placed to play a much bigger role today.

Adam Levin
MAY 24, 2019
Google announced a glitch that stored unencrypted passwords belonging to several business customers, a situation that had been exploitable since 2005. This issue has been fixed and, again, we have seen no evidence of improper access to or misuse of the affected passwords.
Krebs on Security
JUNE 1, 2023
ru , which DomainTools.com says was registered in 2005 to a Konstantin E. Russian motor vehicle records show two different vehicles are registered to this person at the same Moscow address. The most interesting domain name registered to the email address spampage@yahoo.com, fittingly enough, is fitis[.]ru Fetisov from Moscow.
Krebs on Security
NOVEMBER 14, 2024
” Dmitri Golubov, circa 2005. Golubov was arrested in Ukraine in 2005 as part of a joint investigation with multiple U.S. . “My nickname was MikeMike, and I worked with Dmitri Golubov and made technologies for him,” Shefel said. “I’m also godfather of his second son.” Image: U.S. ” Mr.

John Battelle's Searchblog
MAY 25, 2010
By the Fall of 2005 I had assembled a team, an extraordinary group, some of whom are still with us, some of whom, after four years or so, have moved on. A few stats: - FM had under half a million dollars in revenue in 2005. At the time, I owned 100% of FM's voting shares, and to this day, I am still the largest shareholder.

John Battelle's Searchblog
JUNE 9, 2013
I also mentioned that the projects I’d been working on – notably OpenCo and The Book , would have to be retooled given my new commitment to the company I started back in 2005 (when I last wrote a book). In the post, I wrote: I love the book I’m working on, and I don’t plan to abandon it (I’m bringing on a co-author).

AIIM
NOVEMBER 30, 2017
But after 2005, these effects vanish from the measured statistics. Total productivity growth has fallen by two-thirds since 2005, while real GDP growth has averaged about 2 percent per year—all during a period in which the digital economy has continued to grow.”.

John Battelle's Searchblog
JULY 16, 2013
Here’s what I wrote about the issue back in 2005, in The Search : The fact is, massive storehouses of personally identifiable information now exist. In early 2005, I sat down with Sergey Brin and asked what he thinks of the PATRIOT Act, and whether Google has a stance on its implications.

Security Affairs
MARCH 27, 2022
The oldest flaws in the set of 66 recently added issues are dated back to 2005. The new vulnerabilities added to the catalog have to be addressed by federal agencies by April 15, 2022. Microsoft addressed this bug with the release of the February 2022 Patch Tuesday updates.
Security Affairs
NOVEMBER 24, 2022
The experts pointed out that Boa has been discontinued since 2005. ” Microsoft experts explained that despite Boa being discontinued in 2005, many vendors across a variety of IoT devices and popular software development kits (SDKs) continue to use it. ” reads the report published by Microsoft.

Schneier on Security
DECEMBER 14, 2018
I wrote about this exact attack in 2005 and 2009. In the event targets' accounts were protected by 2fa, the attackers redirected targets to a new page that requested a one-time password. This isn't new.

John Battelle's Searchblog
APRIL 26, 2013
image ) Back in 2005 I whipped off a post with a title that has recently become relevant again – “ Traffic of Good Intent.” ” I’m proud to be a co-chair of the group (and yes, the name does come from that 2005 post in these pages).
eSecurity Planet
MARCH 26, 2022
In 2005, the open standard consortium OASIS released SAML 2.0 In 2005, OASIS released 2.0, SAML is an open standard facilitating the communication and verification of credentials between identity providers and service providers for users everywhere. to broad appeal. A year later, SAML 1.0 would become an official OASIS standard.

Security Affairs
SEPTEMBER 3, 2019
XKCD is one of the most popular webcomic platform created by the American author Randall Munroe in 2005, it is a webcomic of romance, sarcasm, math, and language. The popular webcomic platform XKCD has suffered a data breach that exposed data of its forum users, the incident impacted 562,000 subscribers.

Security Affairs
OCTOBER 12, 2018
Experts pointed out that the Shellbot code first appeared in 2005 and is being used by several threat groups, it was also used in the massive crypto-mining campaign that was exploiting the CVE-2017-5638 Apache Struts vulnerability (CVE-2017-5638) in March 2017. “

Imperial Violet
MAY 30, 2017
In 2005 and 2006, a series of significant results were published against SHA-1 [ 1 ][ 2 ][ 3 ]. But the competition itself proved that we do know how to build hash functions: the series of results in 2005 didn't extend to SHA-2 and the SHA-3 process produced a number of hash functions, all of which are secure as far as we can tell.

Security Affairs
SEPTEMBER 4, 2021
. “For example, the SEC brought a number of enforcement actions against individuals and companies who made false and misleading statements about alleged business opportunities in light of damage caused by Hurricane Katrina in 2005. ” reads the alert published by SEC.

John Battelle's Searchblog
JANUARY 3, 2011
2005 Predictions. 2005 How I Did. Related: Predictions 2010. 2010 How I Did. 2009 Predictions. 2009 How I Did. 2008 Predictions. 2008 How I Did. 2007 Predictions. 2007 How I Did. 2006 Predictions. 2006 How I Did. 2004 Predictions. 2004 How I Did.

Security Affairs
JULY 20, 2021
The discovery was casually made several months ago, while experts were configuring a brand new HP printer, and noticed that an old printer driver from 2005 called SSPORT.SYS was triggering an alert by Process Hacker.

The Last Watchdog
MAY 3, 2021
And since 2005 or so, one area of focus has been on sharpening the math formulas that make attribute-based encryption possible. Encryption is an arcane science that has long presented an irresistible challenge to the best and brightest researchers. Top mathematicians have been hammering away at improving encryption since before World War II.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content