U.S. Indicts 2 Top Russian Hackers, Sanctions Cryptex
Krebs on Security
SEPTEMBER 26, 2024
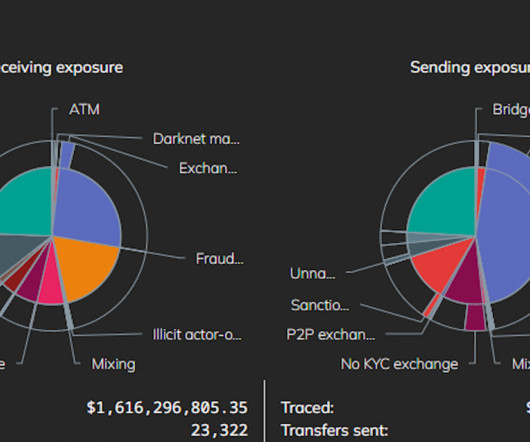
By 2004, v1pee had adopted the moniker “ Vega ” on the exclusive Russian language hacking forum Mazafaka , where this user became one of the more reliable vendors of stolen payment cards. Sergey “Taleon” Ivanov (right) in 2019 in his helicopter with the woman he lives with, flying over a lake north of St.

















Let's personalize your content