The Global Menace of the Russian Sandworm Hacking Team
Data Breach Today
APRIL 17, 2024
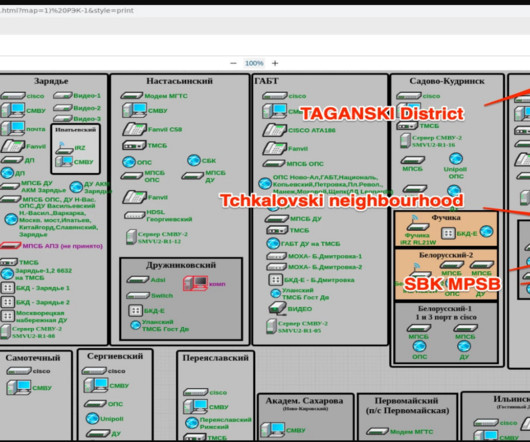
Russian Cyber Sabotage Unit Sandworm Adopting Advanced Techniques, Mandiant Warns Russia's preeminent cyber sabotage unit presents "one of the widest and high severity cyber threats globally," warned Mandiant in a Wednesday report. Mandiant newly designated Sandworm as APT44 to differentiate it from another hacking unit it will still track as APT28.





































Let's personalize your content